Proactively secure your systems by Identifying and remediating critical vulnerabilities with OP Innovate's expert penetration testing and advanced PTaaS platform, WASP.
Expert-Led Penetration Testing Powered by
Automation Technology
Get Started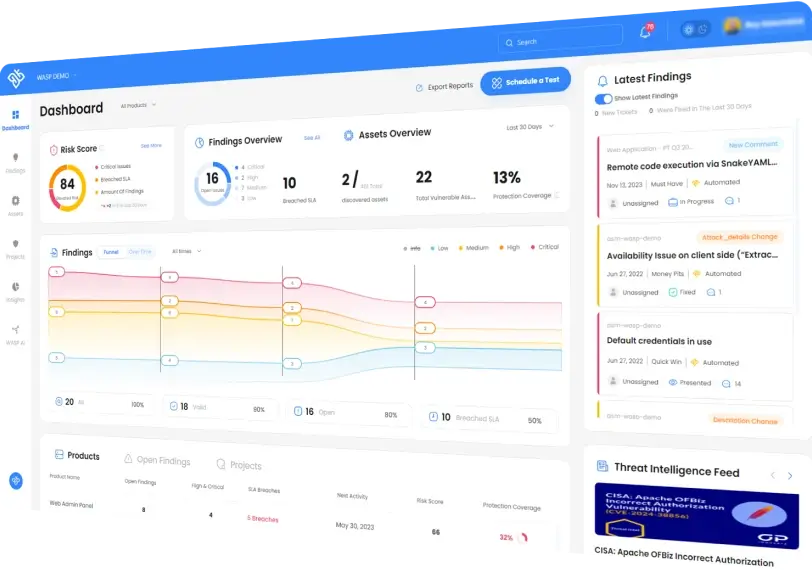
Trusted by
Maximize Security with Proven Penetration Testing
Find all critical vulnerabilities
Comprehensive testing methodologies by accredited professionals ensure no critical vulnerabilities are missed, keeping your systems secure from potential attacks
Avoid unintended disruptions
Prevent unintended disruptions, ensuring smooth operations without system crashes, network congestion, or service interruptions
Reduce False positives
Minimize false positives, helping you focus on real vulnerabilities and saving valuable development hours."
Quickly remediate vulnerabilities
Streamline remediation by creating a direct communication channel between our testers and your developers through WASP.
Perform continuous testing
Guarantee that your app is always secure through continuous automatede penetration testing
Ensure all vulnerabilities get addressed
Our platform allows for efficient management and follow-up of vulnerabilities, ensuring nothing slips through the cracks.









Our Clients Insights
OP Innovate's VDP has helped several organizations improve their vulnerability plan.
Certified by CREST and Offensive Security, our testers use real-world hacking techniques to identify critical vulnerabilities and ensure top-tier security expertise.


OP Innovate has you covered


If you have vulnerabilities, we will find them
Our team is composed of the best offensive security experts in the world, with the credentials to prove it. These experts know how attackers think and how to find vulnerabilities.


Pen-test designed for you
Our penetration tests are tailor-made to your application in order to ensure maximum effectiveness and guarantee your business operations remain unaffected during the test.

Actionable insights
Pen testing reports provide you with actionable insights on real, exploitable vulnerabilities that need to be addressed, with minimal false positives

Streamline remediation
and reduce exposure time with focused plan and ticket integration based on most impactful findings.





Introducing Wasp: Continuous security validation for web

In the ever-increasing threat landscape, security is not an option: OP innovate provides world class cyber expertise with a proven track-record in adversarial and defensive cybersecurity as well as application security, helping global companies to secure their products and forge cyber resilience, readiness, and response.
Explore platform



Schedule a demo / get started

Schedule
a call with one of our defense experts to determine your offensive security objectives and build a free asset map

Discover
your hidden risks and integrate remediation into your dev flow
Remediate
issues and continuously ensure your cyber resilience with WASP state of the art.



Advanced cyber power at your service round the clock
In the ever-increasing threat landscape, security is not an option: OP innovate provides world class cyber expertise with a proven track-record in adversarial and defensive cybersecurity as well as application security, helping global companies to secure their products and forge cyber resilience, readiness, and response.
Learn more about WASP

Application security
Application Pentesting Mobile app testing Secure Code Review Cloud security Appsec consulting
Organisation security
Red Teaming Vuln & risk assessment CISO-as-a-Service Bespoke Cybersecurity service
Incident Response
Quickly and Effectively respond to and resolve Cyber Attacks


A leading cyber consultancy specializing in both defensive and offensive operations
We offer premium incident response, penetration testing (PTaaS) and cyber security consulting services (CISO as a Service), helping organizations worldwide to accelerate containment and remediation of cyber attacks, build cyber resilience and minimize potential brand damage.
Global customers including Fortune 500 leaders across all major market verticals rely on OP Innovate’s expertise, dedication, and ingenuity to swiftly respond to the most sophisticated cyber-attacks, fortify defenses, and prevent future attacks.






FAQS
What types of pen tests does OP Innovate perform?
All pen tests we perform are tailor made to your needs. These include manual pen tests done by our in-house experts, coupled with automated penetration testing using our proprietary WASP platform. While we specialize in web application pen testing, mobile penetration testing, and red teaming with some of the best ethical hackers in the world.
Can your pen testing help in meeting compliance requirements?
Our pen testing team has all the major credentials required to help your organization meet compliance requirements. Prime examples would be companies in the Payment Card Industry Data Security Standard (PCI DSS)
Who Performs the Pent Tests done by OP Innovate?
All of our pen testers are in-house elite specialist. We do not outsource any of our penetration testing team, and only use hand picked veteran security professionals in our team.
How often should pen testing be conducted?
The frequency of pen testing should be based on your organization’s security needs and the level of risk involved. It is recommended to conduct pen tests regularly, especially after significant changes to the system or applications that may introduce new vulnerabilities.









Certifications










Resources highlights
OWASP Top 10 2025: Changes, Challenges, and What They Mean for Web App Security
The Open Web Application Security Project (OWASP) has released an updated OWASP Top 10 list for the first time in four years. This list is…
Read more >

Securing Active Directory: Lessons From the Field
Active Directory interconnects users, devices, and servers in an enterprise, making it a high-value target for attackers. A breach in AD can grant adversaries the…
Read more >

Google Chrome Zero-Day Actively Exploited: CVE-2025-13223
A new high-severity zero-day in Google Chrome is being actively exploited to compromise users through malicious websites. The vulnerability, tracked as CVE-2025-13223, is a type…
Read more >

Critical Remote Code Execution in WatchGuard Firebox VPN Appliances: CVE-2025-9242
A critical vulnerability in WatchGuard Firebox firewalls is being actively exploited to gain remote, unauthenticated code execution on perimeter devices. The flaw, tracked as CVE-2025-9242,…
Read more >

Critical Zero-Day in Samsung Galaxy Devices: CVE-2025-21042
A newly disclosed zero-day vulnerability in Samsung Galaxy smartphones has been actively exploited in the wild to deploy a sophisticated Android spyware framework known as…
Read more >

Critical RCE in CentOS Web Panel (CVE-2025-48703)
CVE-2025-48703 is a critical unauthenticated remote-code-execution (OS command injection) vulnerability in Control Web Panel (CWP / CentOS Web Panel) that allows attackers to inject shell…
Read more >