Cyber Incident Response Services
Contain and recover from cyber attacks swiftly and effectively 24/7
Learn More
Incident Response for a multitude of scenarios
OP Innovate's season incident response team can help your organisation resolve a multitude of different attack types and scenarios

Ransomware (Encryption)
Quickly recover from even the most sophisticated ransomware attacks. Contain the threat, determine root cause, window of compromise, attacker activity, and quantify sensitive information exposed. Where required, negotiate with threat actors, acquire and validate decryption keys, and develop and implement a recovery plan.

Business Email Compromise (BEC)
Recover from unauthorized access to your enterprise email environment. Contain the incident, determine root cause, window of compromise, attacker activity, and quantify sensitive information exposed.

Web Application Compromise
Recover from a web application attack. Contain the threat, analyze logs, review code, quantify exposure or loss of sensitive information, and get recommendations for design hardening countermeasures

Insider Threat
Investigate abuse of privileged access afforded to otherwise trusted employees, including identification of data accessed or misappropriated and/or unwanted actions taken by insiders.

Unauthorized Access
Hunt for historical or ongoing indicators of compromise to identify evidence of unauthorized access or activity (across cloud, email, endpoints).

Malware
Analyze malware samples using open source intel, sandboxing, reverse engineering, and deliver a report, including the behavior and functionality of the malware.
Be Prepared for any cyber attack with ANT Rapid Response Tool
Our incident response process gets a critical head start with the ANT rapid response tool.
ANT provides critical network information on DFIR activities from the earliest moments of the team's engagement.
Coupled together, ANT and our IR team can keep you prepared for a swift response to even the most advance cyber attacks




Our track record
with incident response in cybersecurity

Over 10,000 incident response hours performed in the last 3 years alone

100% satisfied customers exceeding expectations

Experience with all types of cyber incidents

Resolving over 50 cyber incidents every year


Gain Access to all key Stakeholders needed for Incident Response
Our innovative framework includes more than just the technical specialists. In our war room you’ll find a variety of disciplines
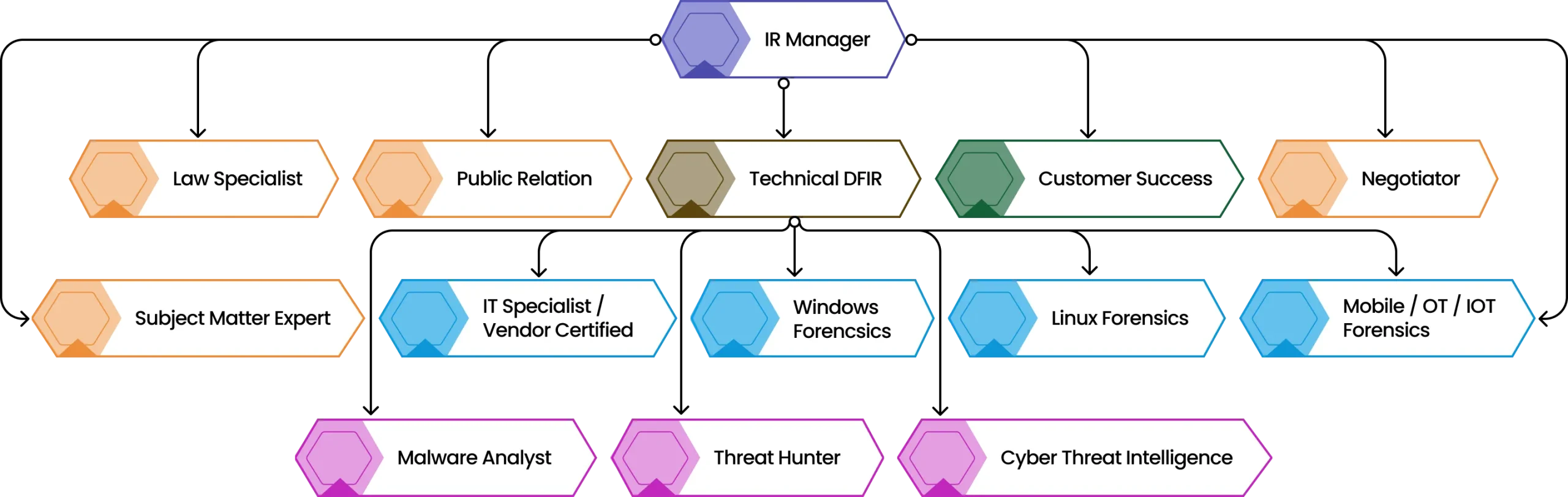





IR Manager -A certified professional with deep expertise in cybersecurity and business analysis. The Incident Response Manager acts as the primary liaison for key customer decision-makers.

Threat Hunter - An offensive security strategist killed in leading offensive operations, capable of tracking and analyzing the steps of attackers.
CTI Specialist - The cyber threat intelligence (CTI) specialist enhances our incident response team by providing critical insights into attacker profiles, interpreting relevant data about the client and their environment.

Crisis Negotiator - Even if your organization doesn’t plan to pay ransom, the negotiator should engage the attacker early to mitigate damage, gather intelligence, and slow their progress to buy time.

PR - Effectively communicating the situation to your customers is crucial for maintaining trust. Our PR specialist ensures that the message of an attack is delivered carefully to avoid sudden drops in stock value.










Accreddited Professionals in Digital Forensics and Incident Response (DFIR)
Certifications
Our team members are all accredited professionals, certified on a variety of sought-after qualifications.
Most of our team SANS GCIH - GIAC Certified Incident Handlers, also holding Practical Malware Analysis qualifications and are OSINT specialists. Their extensive training and experience ensure a rapid and efficient response to incidents, with an unrivaled track record. Our results speak for themselves.










A few examples of some of the customers we've helped recently


Learn how an Incident Response retainer can improve response time and reduce cost
Having a fully prepared incident response plan greatly reduces response time and cost, not to mention unecessary stress. Don't wait for a cyber attack. Receive reduced IR rates and improved response time with an IR retainer

FAQ
What are the benefits of hiring an external incident response team?
Hiring an external incident response team can provide numerous benefits. Some key advantages include expertise, objectivity, rapid response, scalability and flexibility, industry insights, reduced impact and cost-effectiveness.
What steps are involved in OP Innovate’s incident response process?
The incident response process includes identification, containment, eradication, recovery, and lessons learned to improve future security measures.
What is the primary role of OP Innovate’s Incident Response service?
OP Innovate’s Incident Response service is designed to help organizations quickly and effectively respond to and recover from cyber-attacks, minimizing damage and downtime.
How quickly can OP Innovate respond to a cyber incident?
OP Innovate offers 24/7 incident response services, ensuring rapid response to any cyber incident to contain threats and begin recovery efforts immediately.

Related Resources
CVE-2026-20127 & CVE-2022-20775: Active Exploitation of Cisco SD-WAN Systems
A coordinated global campaign targeting Cisco SD-WAN environments has been identified by CISA, NSA, and international partners. Threat actors are actively exploiting a chain of…
Read more >

CVE-2025-49113 & CVE-2025-68461: Actively Exploited Roundcube Webmail Vulnerabilities
Two critical vulnerabilities affecting Roundcube Webmail, a widely deployed web-based email client (commonly bundled with cPanel), have been confirmed as actively exploited in the wild.…
Read more >

CVE-2026-20140: Splunk Enterprise for Windows Local Privilege Escalation
Splunk disclosed a high-severity local privilege escalation (LPE) vulnerability affecting Splunk Enterprise for Windows. An attacker with low-privileged local access may be able to escalate…
Read more >

CVE-2026-22769: Critical Dell RecoverPoint Hardcoded Credential Vulnerability
A critical vulnerability, CVE-2026-22769 (CVSS 10.0), has been identified in Dell RecoverPoint for Virtual Machines, a widely used enterprise backup and disaster recovery solution for…
Read more >

Google Chrome Zero-Day Under Exploitation (CVE-2026-2441)
CVE-2026-2441 is a high-severity use-after-free vulnerability in Google Chrome that is actively exploited in the wild. This marks the first Chrome zero-day patched in 2026.…
Read more >

Actively Exploited BeyondTrust RCE (CVE-2026-1731)
CVE-2026-1731 is a critical remote code execution (RCE) vulnerability affecting BeyondTrust Remote Support and Privileged Remote Access solutions. The flaw is actively exploited in the…
Read more >

What is an Incident Response ?
Uncover your most critical vulnerabilities and logic flaws before an attacker does. Based on OWASP top 10, test for exploits in web applications, APIs, and thick client apps, leveraging attackers' Tactics, Techniques, and Procedures (TTPs).

Efficient Scans
PTaaS utilizes automated scanning tools to efficiently identify vulnerabilities in web applications, APIs, and network/cloud devices. This saves time and effort compared to manual scanning processes.


Expert Analysis
The human assessment aspect of PTaaS involves security experts with industry accreditations who analyze the results of the scans. Their expertise enhances the detection of complex vulnerabilities and provides critical insight and analysis.


Risk Prioritization
PTaaS not only identifies vulnerabilities but also validates and rates their risk against risk databases. This risk-based approach allows organizations to prioritize remediation efforts and focus on addressing the most severe vulnerabilities first, providing you and your product team with the best return on PT investment over time.