
Proactively secure your systems by Identifying and remediating critical vulnerabilities with OP Innovate's expert penetration testing and advanced PTaaS platform, WASP.
Expert-Led Penetration Testing Powered by
Automation Technology
Get Started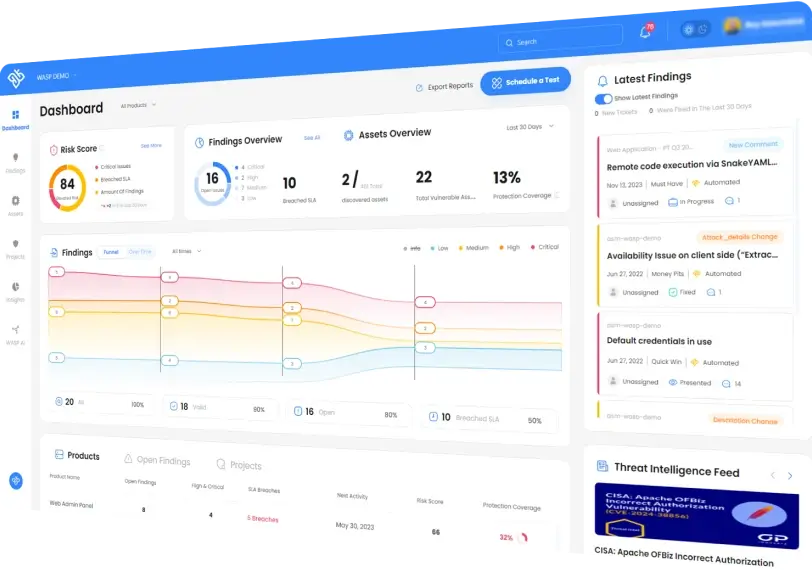
Trusted by
Maximize Security with Proven Penetration Testing
Find all critical vulnerabilities
Comprehensive testing methodologies by accredited professionals ensure no critical vulnerabilities are missed, keeping your systems secure from potential attacks
Avoid unintended disruptions
Prevent unintended disruptions, ensuring smooth operations without system crashes, network congestion, or service interruptions
Reduce False positives
Minimize false positives, helping you focus on real vulnerabilities and saving valuable development hours."
Quickly remediate vulnerabilities
Streamline remediation by creating a direct communication channel between our testers and your developers through WASP.
Perform continuous testing
Guarantee that your app is always secure through continuous automatede penetration testing
Ensure all vulnerabilities get addressed
Our platform allows for efficient management and follow-up of vulnerabilities, ensuring nothing slips through the cracks.









Our Clients Insights
OP Innovate's VDP has helped several organizations improve their vulnerability plan.
Our Clients Insights
Certified by CREST and Offensive Security, our testers use real-world hacking techniques to identify critical vulnerabilities and ensure top-tier security expertise.


OP Innovate has you covered


If you have vulnerabilities, we will find them
Our team is composed of the best offensive security experts in the world, with the credentials to prove it. These experts know how attackers think and how to find vulnerabilities.


Pen-test designed for you
Our penetration tests are tailor-made to your application in order to ensure maximum effectiveness and guarantee your business operations remain unaffected during the test.

Actionable insights
Pen testing reports provide you with actionable insights on real, exploitable vulnerabilities that need to be addressed, with minimal false positives

Streamline remediation
and reduce exposure time with focused plan and ticket integration based on most impactful findings.





Introducing Wasp: Continuous security validation for web

In the ever-increasing threat landscape, security is not an option: OP innovate provides world class cyber expertise with a proven track-record in adversarial and defensive cybersecurity as well as application security, helping global companies to secure their products and forge cyber resilience, readiness, and response.
Explore platform



Schedule a demo / get started

Schedule
a call with one of our defense experts to determine your offensive security objectives and build a free asset map

Discover
your hidden risks and integrate remediation into your dev flow
Remediate
issues and continuously ensure your cyber resilience with WASP state of the art.



Advanced cyber power at your service round the clock
In the ever-increasing threat landscape, security is not an option: OP innovate provides world class cyber expertise with a proven track-record in adversarial and defensive cybersecurity as well as application security, helping global companies to secure their products and forge cyber resilience, readiness, and response.
Learn more about WASP

Application security
Application Pentesting Mobile app testing Secure Code Review Cloud security Appsec consulting
Organisation security
Red Teaming Vuln & risk assessment CISO-as-a-Service Bespoke Cybersecurity service
Incident Response
Quickly and Effectively respond to and resolve Cyber Attacks


A leading cyber consultancy specializing in both defensive and offensive operations
We offer premium incident response, penetration testing (PTaaS) and cyber security consulting services (CISO as a Service), helping organizations worldwide to accelerate containment and remediation of cyber attacks, build cyber resilience and minimize potential brand damage.
Global customers including Fortune 500 leaders across all major market verticals rely on OP Innovate’s expertise, dedication, and ingenuity to swiftly respond to the most sophisticated cyber-attacks, fortify defenses, and prevent future attacks.






FAQS









Certifications










Resources highlights
Malicious “AI Assistant” Chrome Extensions Stealing Credentials and Email Data
A malicious browser extension campaign dubbed AiFrame has been identified distributing fake AI assistant tools through the Chrome Web Store. At least 30 malicious extensions,…
Read more >
CVE-2026-21509: Actively Exploited Microsoft Office Security Bypass
CVE-2026-21509 is a zero-day security feature bypass vulnerability in Microsoft Office that has been confirmed as actively exploited in the wild. The flaw allows adversaries…
Read more >

Guidance to Address Ongoing Exploitation of Fortinet SSO Vulnerability (CVE-2026-24858)
CVE-2026-24858 is a critical authentication bypass in FortiCloud Single Sign-On (SSO) that can allow an attacker with a FortiCloud account and a registered device to…
Read more >

CVE-2024-37079: VMware vCenter Server DCERPC Heap Overflow (RCE)
CVE-2024-37079 is a critical remote code execution (RCE) vulnerability in VMware vCenter Server caused by a heap overflow in the DCERPC protocol implementation. On January…
Read more >

CVE-2026-24061: GNU Inetutils telnetd Remote Authentication Bypass
CVE-2026-24061 is a pre-authentication remote authentication bypass in GNU Inetutils telnetd. The flaw carries a Critical CVSS:3.1 severity score of 9.8 and allows an attacker…
Read more >

CVE-2026-0227: PAN-OS GlobalProtect Denial-of-Service Vulnerability
CVE-2026-0227 is a high-severity denial-of-service vulnerability affecting Palo Alto Networks PAN-OS and Prisma Access deployments where GlobalProtect Gateway or Portal is enabled. The flaw allows…
Read more >













