Meet SOC 2 Requirements with a SOC 2 certified company
Achieving and maintaining SOC 2 compliance is vital for protecting customer trust and projecting a strong security posture. At OP Innovate, we empower organizations to meet SOC 2 compliance standards with our cutting-edge WASP platform that incorporates Penetration Testing as a Service (PTaaS).
Contact Us to Achieve SOC2 Compliance with WASP
How WASP Helps You Achieve SOC 2 Compliance
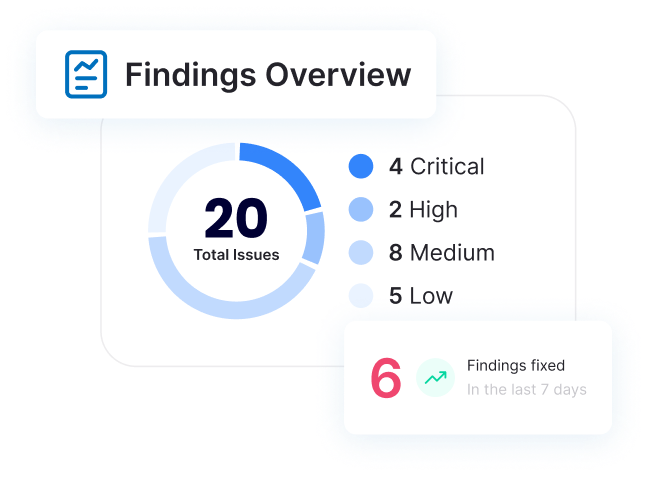
Achieving SOC 2 compliance requires effective risk identification and mitigation, especially for security vulnerabilities. OP Innovate’s WASP platform simplifies this with continuous penetration testing and actionable insights.
Here’s how we make SOC 2 compliance achievable:
Continuous Penetration Testing
WASP enables ongoing identification of vulnerabilities across your systems, ensuring your organization stays ahead of potential threats. This aligns with the Security and Confidentiality Trust Service Criteria.
Real-Time Remediation Guidance
Our platform doesn’t just find vulnerabilities—it prioritizes them based on risk and provides clear, actionable remediation guidance, supporting the Processing Integrity criterion.
Audit-Ready Reporting
WASP generates comprehensive reports tailored for SOC 2 audits, giving your auditors the information they need while saving you time.
Proactive Risk Management
With WASP, you gain continuous insights into your security posture, helping you demonstrate the Availability of your systems to auditors and customers.
Meeting Specific SOC 2 Penetration Testing Requirements
Relevant SOC 2 Controls:
A1.1
CC1.2
CC3.2
CC7.1
CC7.2
CC9.2
Risk Assessment and Management
Our expert team has years of experience conducting and managing risk assessments across various industries and organization sizes. Our researchers collaborate with clients to identify risks, prioritize mitigation strategies, and develop comprehensive compliance plans tailored to meet SOC 2 standards.
Relevant SOC 2 Controls:
CC3.2
CC5.1
CC5.2
CC6.6
CC6.7
CC7.1
CC7.2
Vulnerability Scanning and Continuous Threat Exposure
OP Innovate combines expert-led, CREST-certified manual testing with the automated capabilities of our WASP platform to deliver unmatched vulnerability detection and streamlined remediation. This approach ensures a robust and SOC 2-compliant security posture while continuously monitoring and identifying new threats.
Relevant SOC 2 Controls:
CC2.1
CC2.2
CC3.3
CC6.7
CC7.3
CC7.4
CC7.5
Incident Response
OP Innovate offers an Incident Response (IR) Retainer service, ensuring your organization is prepared to respond to incidents at a moment's notice. Our expert team helps identify, contain, and remediate threats while aligning with SOC 2 requirements for detection and monitoring procedures.
Relevant SOC 2 Controls:
CC3.2
CC4.1
CC5.1
CC5.6
CC5.8
CC6.1
Threat Intelligence Integration
OP Innovate's WASP platform integrates cutting-edge threat intelligence capabilities, allowing organizations to scan assets and receive actionable insights. This integration identifies vulnerabilities informed by real-time threat data, empowering organizations to address emerging risks effectively and maintain SOC 2 compliance.
Relevant SOC 2 Controls:
CC7
CC8.1
CC5.3
Patch Management
OP Innovate’s patch management capabilities identify outdated software and recommend timely upgrades or patches. This quickly closes security gaps resulting from unpatched vulnerabilities, in line with SOC 2 standards.
What is SOC 2 Compliance?
SOC 2 (Service Organization Control 2) is a gold-standard framework for managing customer data, developed by the American Institute of CPAs (AICPA). It focuses on five Trust Service Criteria (TSCs): Security, Availability, Processing Integrity, Confidentiality and Privacy.
SOC 2 compliance is essential for any company handling sensitive customer data, particularly in industries such as SaaS, finance, healthcare, and technology. Many companies expect their vendors to be compliant and use SOC 2 compliance as a cornerstone of their 3rd party risk strategy, selecting vendors who have type II reports over those who don’t.

Trusted by
OP Innovate Penetration Testing for SOC 2
At OP Innovate, we understand that compliance is about more than just checking boxes—it’s about building trust. Here’s what sets us apart:
Expert-Led Testing
Our penetration testing services combine the expertise of seasoned, CREST-certified security professionals with the efficiency of automation.
Customized Solutions
Every business is unique. WASP allows you to tailor penetration testing and compliance strategies to meet your specific needs.
Seamless Integration
Our platform integrates seamlessly into your existing workflows, minimizing disruption while maximizing results.

Strong Collaboration
Strong working relationships with the top AICPA accredited audit companies including the Big Four.
Resources highlights
Zoom Tackles Critical Security flaws Head-On with New Patches
Keeping our online conversations safe is a big deal, and Zoom knows it. The popular video call service recently rolled out fixes to patch up…
Read more >

nOAuth – Microsoft OAuth Misconfiguration can result in a full account takeover.
A significant flaw known as nOAuth has come to light, discovered by the diligent security team at Descope. This flaw, found in Microsoft Azure AD…
Read more >

Penetration Testing for Compliance: Why It’s Essential for Your Organization’s Security, Not Just for Compliance
Penetration testing is a process of testing your organization’s security by simulating an attack. Many organizations conduct pen testing as part of their compliance requirements.…
Read more >

Take the First Step Toward Becoming SOC 2 Compliant
Ready to streamline your road toward SOC 2 compliance? Partner with OP Innovate and leverage the power of WASP to simplify your compliance journey while strengthening your security posture.
Contact us today to schedule a demo and see how WASP can help you achieve SOC 2 compliance with confidence.












