As the cybersecurity environment becomes becomes more dynamic with each passing year, rapid vulnerability detection and remediation have become non-negotiable for maintaining a robust security posture.
That’s precisely why we launched WASP (Web Application Security Platform) back in 2019. By creating a solution that can not only detect vulnerabilities quickly, but also help our clients remediate them, we empower organizations to proactively address security risks and dramatically reduce their attack surface.
As we move into the new year, we’d like to share the core features that make WASP the ideal continuous threat exposure management (CTEM) and vulnerability detection and remediation platform on the market.
The Challenges of Vulnerability Remediation in 2025
Let’s start by understanding why businesses struggle to address the vulnerabilities that have the largest potential impact:
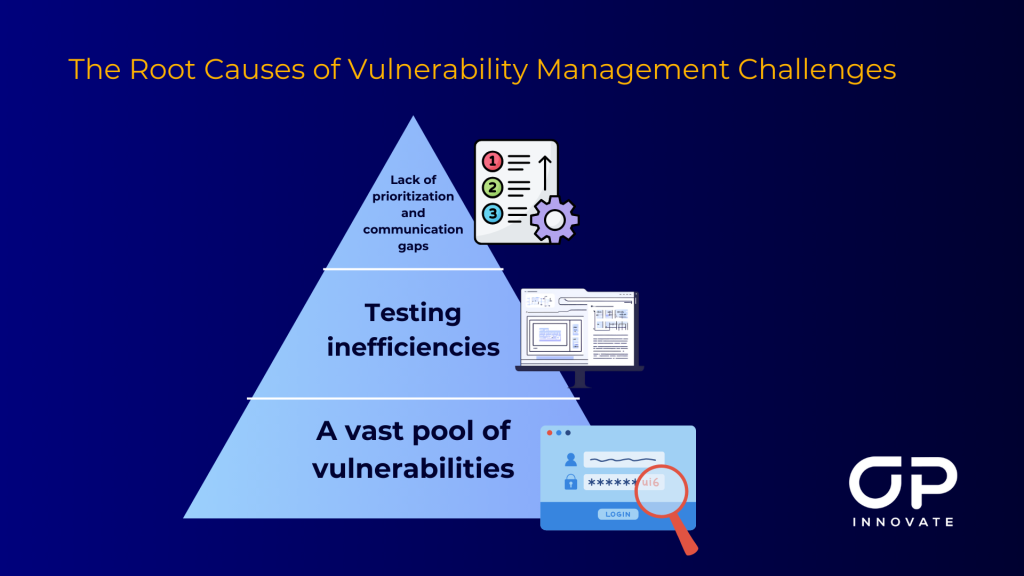
- A vast pool of vulnerabilities
Attackers now have access to a massive pool of exploitable vulnerabilities, which are not only available on the Dark Web, but also through public vulnerability disclosures such as the MITRE CVE database and bug bounty programs.
- Shortened timelines for attackers to weaponize vulnerabilities
Not only do attackers have more vulnerabilities to exploit, but it takes them less time to weaponize them and launch attacks. With automated tools, exploit kits, and AI-driven methods, attackers can quickly turn newly disclosed vulnerabilities into actionable exploits.
Studies show that the median time to exploitation for critical vulnerabilities has decreased to just days, leaving organizations with a narrower window to identify and remediate these risks.
- Vulnerability testing inefficiencies
Traditional, strictly manual-focused penetration testing isn’t practical enough to keep up with the rapid pace of modern vulnerability discovery. Since attackers are strongly using automation, defenders must also adopt it in some capacity to keep up.
- Lack of prioritization of vulnerabilities
Organizations are often overwhelmed with large volumes of vulnerabilities identified during scans, many of which may not pose an immediate threat. Without a clear system for prioritization, teams waste valuable time addressing low-risk issues while critical vulnerabilities remain exposed.
- Communication gaps between security and dev teams
The final problem lies in the inefficient communication between security and development teams. Security professionals often provide developers with generic or unclear remediation guidance, while developers may prioritize functionality over security due to time constraints.
What Makes WASP Stand Out in 2025
WASP is uniquely designed to address the critical challenges of vulnerability remediation in 2025.
WASP combines the speed and efficiency of automated testing, with the skill and ability to discover nuance vulnerabilities through manual validation by CREST-certified experts. This hybrid approach ensures comprehensive and accurate vulnerability detection, addressing both common exploits and complex, hidden threats that automated tools alone might miss.
All findings and security insights are delivered in seamless, easy-to-navigate dashboards and reports that provide tailored views for different stakeholders, from high-level summaries for executives to detailed technical data for security teams and developers.
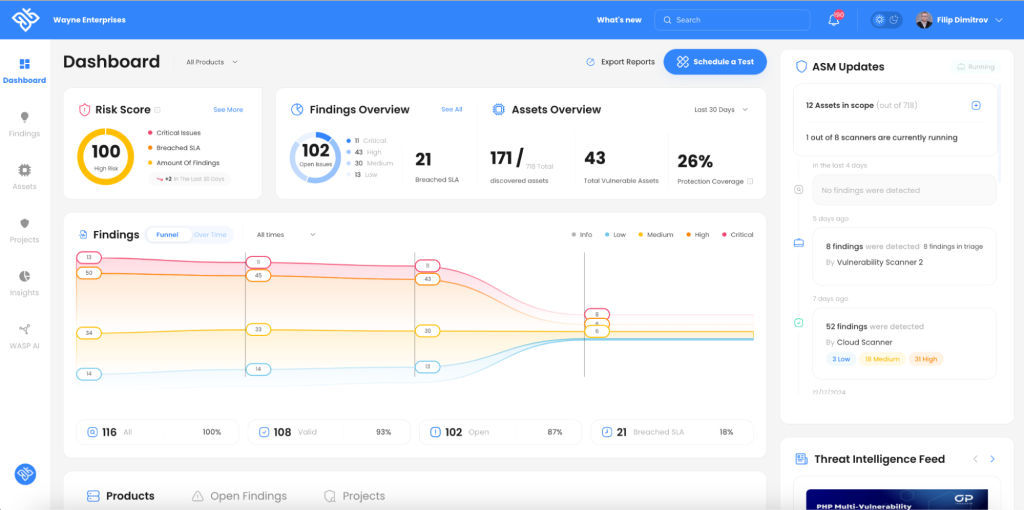
The main dashboard in WASP
WASP is more than a detection platform; it’s a solution that emphasizes actionable insights and collaboration. Its intuitive dashboards and automated workflows help teams prioritize the most critical vulnerabilities, reducing time spent on false positives or low-risk issues.
The platform’s flexibility and scalability make it a fit for organizations of all sizes, from startups to enterprises. Whether monitoring a single application or managing hundreds of assets across multi-cloud environments, WASP scales effortlessly to meet your needs.
Core Features
- Real-Time Vulnerability Detection
WASP uses advanced automated scanning tools to constantly and proactively identify threats. Its real-time scanning capabilities mean that vulnerabilities are detected as soon as they appear, allowing organizations to address them before attackers can exploit them.
- Prioritization of Vulnerabilities
In WASP, you always know which vulnerabilities to address first, thanks to its risk-based scoring system. WASP evaluates vulnerabilities based on their severity, exploitability, and potential impact on your systems, ensuring that your team focuses on the most critical issues to minimize risk.
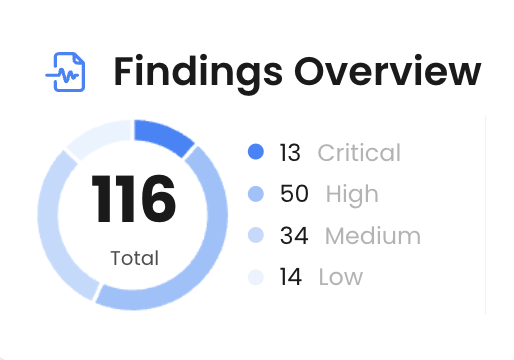
All findings have a severity label ranging from Low to Critical
- Actionable Remediation Guidance
Identifying vulnerabilities is only half the battle. WASP delivers clear, prioritized remediation steps, ensuring that teams know exactly what to do to mitigate risks.
- Integration With Dev Workflows
WASP integrates seamlessly with ticketing systems like Jira, making it easy for developers to track, prioritize, and address vulnerabilities directly within their existing workflows. This integration ensures that security becomes a natural part of the development process, significantly reducing MTTR.
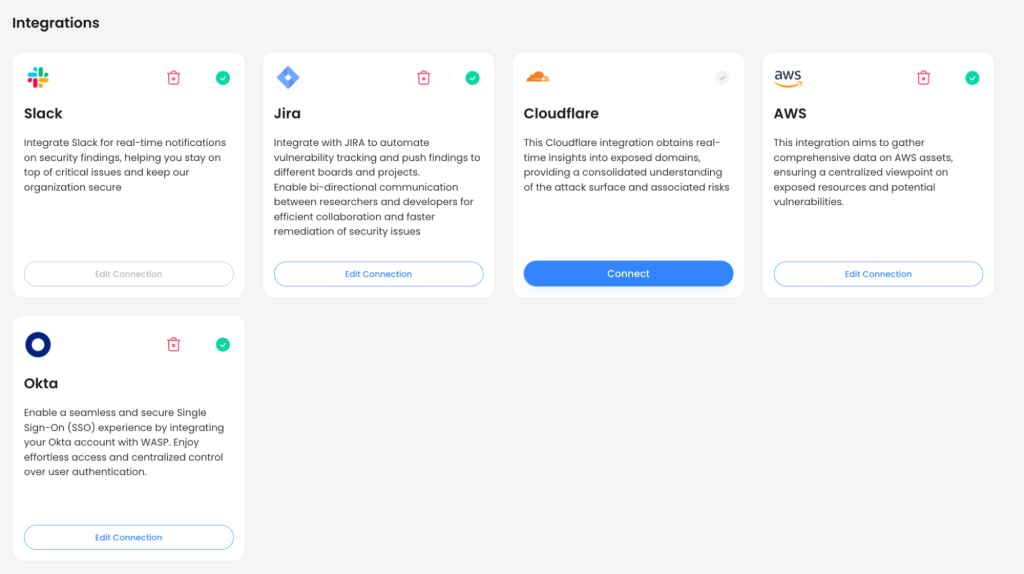
The main WASP integrations (more are available through our Community Library)
- On-demand Access to CREST-Certified Experts
Our seasoned team is always available to dive deeper into security findings to provide further guidance, or validate automated scans to ensure critical vulnerabilities are accurately identified and false positives are minimized.
Use Cases: How WASP Addresses Emerging Threats
Identifying Zero-Day Threats
Discovering zero-days in your tool stack before attackers drastically reduces your risk exposure. WASP allows you to schedule regular penetration tests conducted by an experienced, CREST-certified team that will stress-test your applications, find any vulnerabilities that could be exploited, and provide actionable guidance to help you remediate them quickly and effectively.
Scheduling a pen test in WASP is easy. All you have to do is select the time and assets you want tested, and our team will take care of the rest, including delivering a detailed report of all findings and remediation steps.
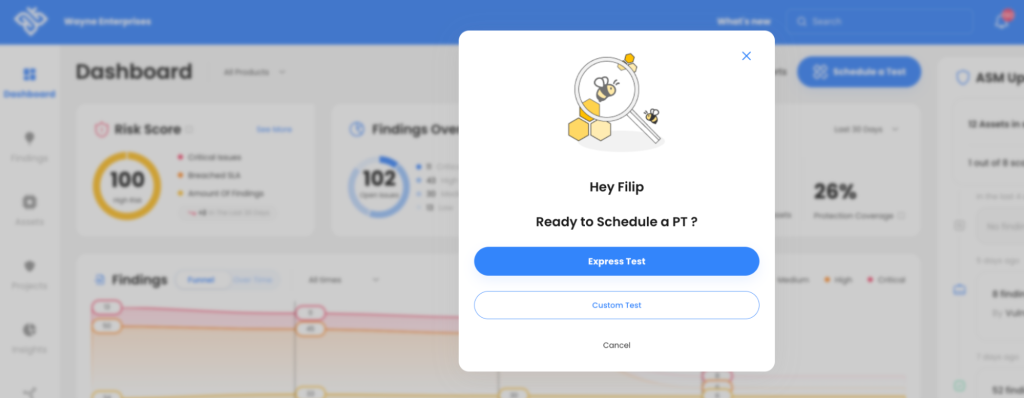
Scheduling a pen test in WASP
Regulatory Compliance
Proactive security is becoming a cornerstone of regulatory compliance. WASP can help organizations meet and exceed the requirements of key frameworks such as SOC 2, ISO 27001, GDPR, and more.
There are two essential WASP features that make it an invaluable tool for regulatory compliance:
- Ongoing testing to identify and reduce risk
With WASP’s proactive approach, organizations have a way to continuously identify and reduce risk, in line with popular compliance frameworks.
- Detailed reporting to simplify audits
The platform generates audit-ready reports that include a comprehensive breakdown of vulnerabilities, remediation actions, and compliance alignment. These reports streamline the audit process, making it easier for organizations to demonstrate adherence to regulatory standards and reduce administrative overhead.
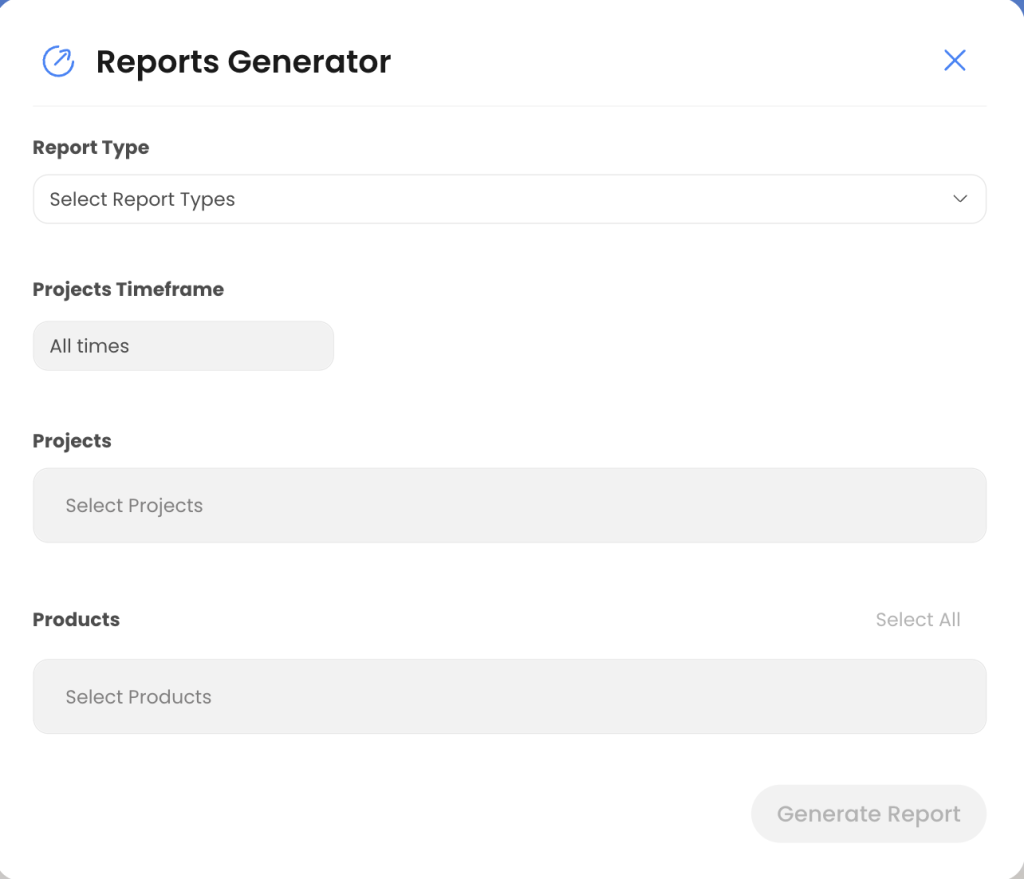
The Reports Generator
Managing Cloud Security Risks
With many organizations migrating to the cloud, WASP is emerging as a comprehensive solution that can detect vulnerabilities ranging from simple misconfigurations, to inherent flaws in cloud infrastructure.
Our automated scanners and manual penetration testing capabilities work together to uncover these vulnerabilities in real time to ensure your cloud implementation remains resilient.
WASP in Action: Metrics That Matter
When evaluating the effectiveness of a vulnerability management platform, metrics provide the clearest picture of its impact. WASP delivers measurable improvements across all critical performance indicators.
Time to Remediate
Don’t take our word for it – our clients are reporting an up-to 75% reduction in their Mean Time to Remediate (MTTR):


Coverage of Vulnerable Assets
WASP ensures comprehensive testing across an organization’s entire infrastructure, leaving no gaps in security. By combining automated scanning with manual penetration testing, the platform identifies vulnerabilities across applications, APIs, cloud environments, and on-premise systems.
This holistic approach ensures an up to 95% asset coverage.
Reduction in Risk Exposure
On average, organizations report a 50% reduction in their exploitable attack surface within the first six months of using WASP. The platform’s real-time testing capabilities and detailed reporting enable organizations to continously track progress, measure risk reduction, and refine their security strategies.
Together, these metrics showcase WASP’s ability to deliver unparalleled protection while streamlining the vulnerability management process.
Prepare for 2025’s Threats with WASP
Proactive security and vulnerability management must become a core component of every security program in 2025.
To let you experience the power of WASP first-hand, OP Innovate is offering a month-long free trial of the platform.
During the trial, you’ll gain access to WASP’s full suite of features, including:
- Continuous Penetration Testing to uncover vulnerabilities in real time.
- Actionable Insights and Reporting to streamline remediation efforts.
- Customizable Dashboards that provide tailored metrics for your team.
- Seamless Integration with your existing CI/CD pipelines.
To start your free trial, register for an account through the WASP registration page: https://wasp.op-c.net/register
For any additional questions, or to schedule a demo of the platform, please contact OP Innovate.










