In an effort to improve security test result relevance and coverage, we are excited to announce a significant upgrade to our WASP platform – the addition of authenticated scanning.
Authenticated scanning combines automation with human expertise to produce more accurate and detailed vulnerability assessments. It uncovers security flaws that are only visible when a user is authenticated.
What is authenticated scanning?
Authenticated scanning is a type of security testing in which the scanner logs into the system or application being tested with valid credentials. This method provides the scanner with access to internal parts of the system that are not accessible to unauthenticated users, allowing for a more comprehensive assessment of security vulnerabilities.
How it works
- Credential setup: Before the scan begins, valid credentials (either user credentials or specific test accounts) are configured within the WASP scanner. These credentials should have the appropriate level of access to explore various functionalities of the application as different types of users (like a regular user, admin, or special roles).
- Logging in: The scanning tool uses these credentials to log into the application. This process is similar to how a legitimate user would access the system, ensuring that the scanner experiences the application as a user would.
- Session management: Once logged in, the scanner maintains the session just as a user would, utilizing session tokens or cookies that the application provides. This allows the scanner to navigate through the application and perform actions that require authentication.
- Access and test protected areas: With authentication, the scanner can access parts of the application that are not visible or accessible to unauthenticated users. Most websites and applications grant additional features to authenticated users such as updating user profiles, filling data forms or inviting other users. As these features are now accessible to the scanner, it is possible to expose vulnerabilities related to these operations.
- Vulnerability detection: The scanner tests for a wide range of vulnerabilities, including those related to improper access controls, insecure direct object references, cross-site request forgery, and more. Because the scanner can interact as a logged-in user, it can also test for flaws in business logic that may not be apparent in an unauthenticated scan.
- Reporting: After the scan is completed, a report is generated within the WASP platform, detailing any vulnerabilities found, including where they are located and the potential impact. This report includes recommendations for vulnerability remediation.
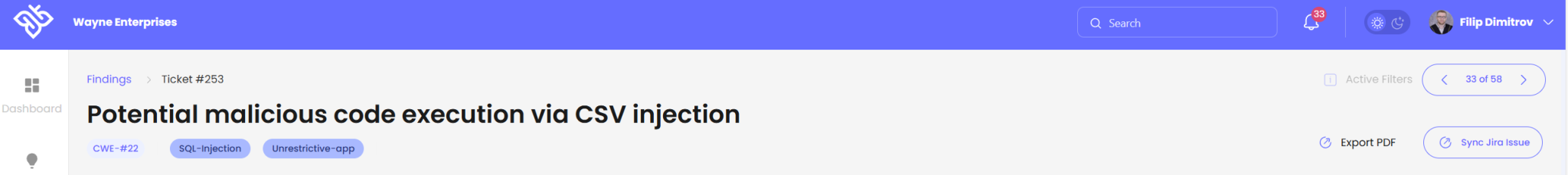
Vulnerability discovered via authenticated scanning inside the WASP platform
The main benefits of authenticated scanning
- Enhanced coverage: Authenticated scans can access and test all areas of the application, just as a legitimate user would. This comprehensive coverage ensures that more of the application is scrutinized, leaving fewer blind spots.
- Deeper insight: By interacting as an authenticated user, the scanner can perform actions that uncover deeper, more subtle vulnerabilities that would be inaccessible in an unauthenticated state.
- Increased relevance: The findings from authenticated scans are typically more relevant, providing insights into actual risks that affect authenticated users.
Unauthenticated vs. authenticated scans
Unauthenticated scanning limits the scope to merely the “perimeter” of an application, akin to checking the locks on the doors without being able to assess the integrity of the entire building. Without authentication, the scanner cannot interact with or test the full range of functionalities that an authorized user would access. This severely restricts the ability to discover vulnerabilities within the application’s internal features and functionalities.
Authenticated scanning, in contrast, provides a deeper and more accurate view by testing the application through the lens of a legitimate user. By accessing all areas of the application, authenticated scanning can uncover flaws in internal workflows, access controls, and functionalities that are only exposed to authenticated users. This capability makes it indispensable for thorough and effective application security testing.
Since most MSPs rely on unauthenticated scanning, they often miss crucial security flaws that only manifest once a user is logged in.
For complete visibility into your security posture, it’s best to combine authenticated scanning with regular penetration testing and continuous vulnerability assessments.
CTEM and Authenticated Scanning: A Powerful Combination
Integrating Continuous Threat Exposure Management (CTEM) into your security strategy ensures a proactive approach to identifying and mitigating threats. CTEM involves ongoing monitoring, assessment, and remediation of security risks, which aligns seamlessly with the enhanced insights provided by authenticated scanning. This combination allows organizations to maintain a robust security posture by continually adapting to new threats and vulnerabilities.
Authenticated scanning within the WASP platform, combined with CTEM, offers a dynamic defense mechanism. While authenticated scanning exposes deeper vulnerabilities by simulating legitimate user access, CTEM ensures these findings are continuously monitored and addressed.
Access authenticated scanning with WASP
OP Innovate’s WASP platform is the ultimate security testing and attack surface management tool tailored for application security.
With the latest addition of authenticated scanning, WASP has enhanced its capabilities to provide a more in-depth and precise analysis of security vulnerabilities. This powerful feature allows users to test applications from the perspective of both authenticated and unauthenticated states, offering a comprehensive view of security weaknesses across the application.
Some of the key benefits of WASP include:
- Detailed analysis of the most important findings, complete with remediation suggestions
- Feeds vulnerability data directly into developers’ workflow
- Regular updates and new features (you can track our release notes here.)
- A team of highly-trained professionals who are always there to deliver immediate feedback and dive deep into security findings
Contact us now to get started.









