When it comes to red team operations, the tools you choose can make or break the engagement. From initial reconnaissance to post-exploitation, having a streamlined, battle-tested toolkit is essential for both speed and success.
At OP Innovate, our CREST-certified penetration testers rely on a curated set of tools designed to uncover vulnerabilities, validate exposure, and guide real remediation. While many lists throw every tool in the book at you, we’ve narrowed it down to our six favorite tools, each with a unique role in the offensive security kill chain.
And at the top of that list is WASP, our own orchestration and penetration testing platform, which brings everything together.
WASP (Pentesting Orchestration, Automation & Reporting)
Use case: Centralized scanning, manual testing workflows, report generation
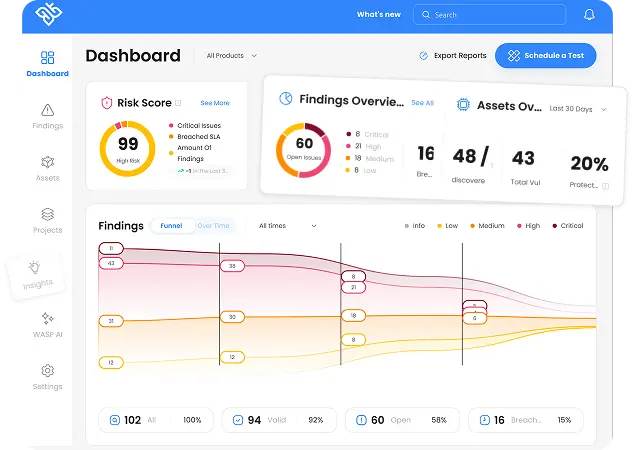
The WASP dashboard
WASP is more than a tool. It’s our command center. Designed by OP Innovate to streamline complex testing engagements, WASP lets us combine automated scanning with expert manual testing to triage findings in real-time, and communicate clearly with clients as we go.
Instead of jumping between different scanners, terminals, and reporting tools, WASP integrates core capabilities, including:
- Automated vulnerability scanners for web apps, networks, and cloud environments
- External and internal attack surface mapping
- Credential validation and lateral movement modules
- Real-time issue triage and remediation tracking
Our vulnerability and asset discovery scanners are based on best-in-class tools, such as Nessus, Bbot, and Nuclei, allowing security teams to move from recon to reporting without ever leaving the platform.
WASP filters out noise, prioritizes real issues, and transforms red team findings into actionable remediation tickets.
“With WASP, we don’t just find vulnerabilities; we help teams fix them. It’s the glue that connects the attack to the defense.”
Yehonatan Narizi, OSCP, OSWE
Security Researcher, OP Innovate
Whether you’re managing a short-term engagement or running continuous testing on a high-risk asset, WASP brings structure to the chaos of offensive security, streamlining both execution and communication between red and blue teams.
Nmap (Reconnaissance and Network Mapping)
Use case: Network discovery, port scanning, service enumeration
Every good red teamer knows the mission starts with recon. Nmap (and its GUI cousin Zenmap) is our go-to for building an initial attack surface map. It tells us what’s exposed, what’s alive, and what versions of software are running, often revealing misconfigurations or unpatched services that are ripe for exploitation.
Even a basic scan (nmap -sS -sV -T4) gives valuable insights. We also use custom scripts and NSE (Nmap Scripting Engine) to dive deeper during pre-engagement mapping.
Nuclei (Vulnerability Scanning)
Use case: Scanning web apps for known vulnerabilities and misconfigurations using community-driven templates
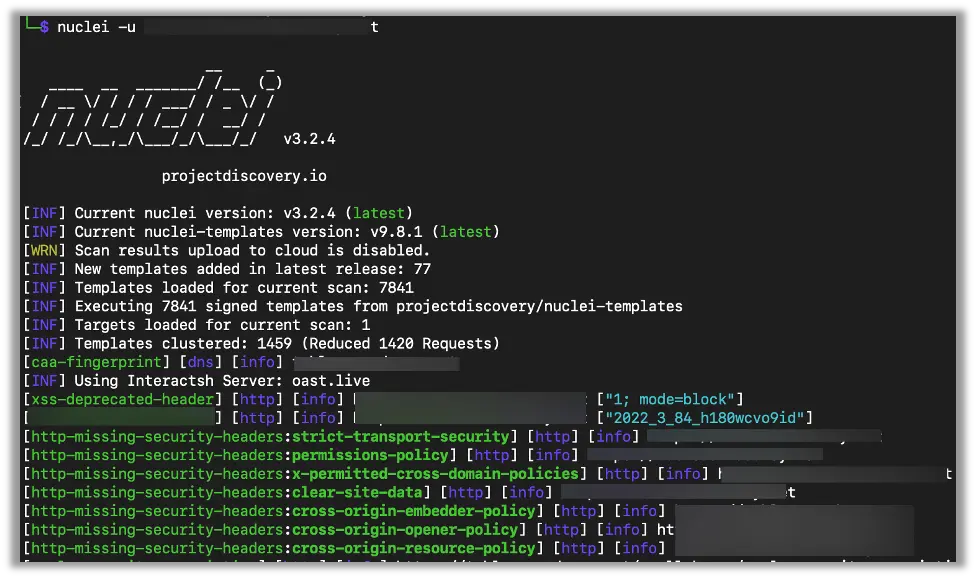
For fast, scalable scanning, Nuclei is our go-to. It employs a massive, modular library of community-maintained templates to detect a wide range of issues, such as missing security headers, exposed files, vulnerable software versions, misconfigurations, CVEs, and even SSRF or subdomain takeover patterns.
Nuclei is very fast and highly customizable
- Lightning-fast performance: Capable of running thousands of templates in parallel with intelligent clustering, delivering results in minutes .
- Highly customizable: You can filter templates by tags (e.g., cve, rce, cloud), create your own, or integrate custom workflows, making it a flexible tool for any scope
- Seamless integration: Works smoothly with reconnaissance tools like subfinder and httpx in automated CI/CD or pentest pipelines
BloodHound w/SharpHound (Active Directory Attack Path Mapping)
Use case: Mapping privilege escalation paths in AD environments
In enterprise environments, Active Directory remains the main battlefield. BloodHound, powered by the data collected via SharpHound, is our key tool for mapping it out.
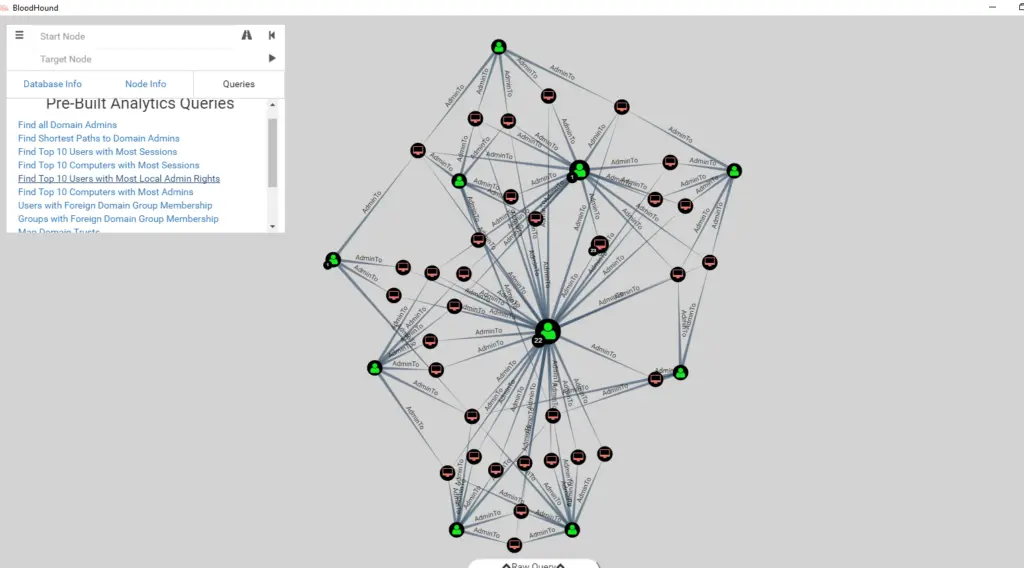
- SharpHound gathers data from domain controllers and machines, including sessions, group memberships, ACLs, trusts, and delegation settings by using native APIs and LDAP queries
- BloodHound visualizes that data in an interactive graph (see screenshot above), allowing analysts to query and explore beyond manual enumeration .
With just a few clicks, we can identify and exploit complex escalation chains, like a low-privileged user who can write to a service account in Backup Operators, which in turn can lead straight to Domain Admin compromise
This tool is essential in assumed-breach scenarios, where initial access is already obtained and the goal is to move laterally toward critical systems. BloodHound’s ability to automatically outline shortest paths and track trust relationships makes it a staple in modern red team operations.
Impacket (Lateral Movement & Remote Code Execution)
Use case: Using captured credentials to pivot across systems and execute remote commands stealthily
Impacket is a central part of our lateral movement strategy. It’s a suite of Python scripts and libraries that enable us to interact with Windows hosts over SMB, RPC, and WMI without writing files to disk.
Modules like wmiexec.py, smbexec.py, and psexec.py allow remote command execution using valid credentials, making it possible to move laterally, collect additional information, or escalate privileges while minimizing detection.
Once our red team has a foothold inside a network, Impacket tools often come into play. For example, after obtaining user credentials or hashes, we might use psexec.py (an Impacket module) to execute a payload on another machine using SMB and a valid credential.
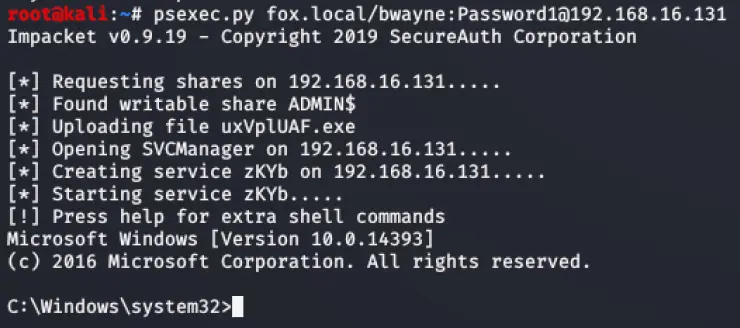
Successful remote code execution using Impacket’s psexec.py
From a CISO’s viewpoint, seeing Impacket show up in a penetration test report is a sign that critical post-exploitation actions were possible in the environment, underlining the need for better lateral movement defenses.
Responder (Hash Capture via LLMNR/NBT-NS Poisoning)
Use case: Capturing NTLM hashes on internal networks
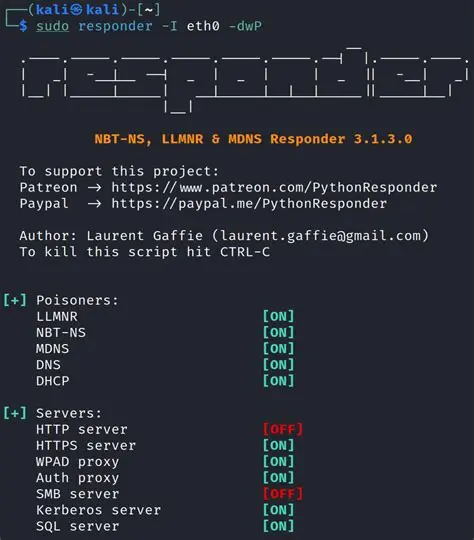
In many internal networks, Windows clients rely on fallback name resolution protocols, LLMNR and NBT‑NS, when DNS queries fail. Responder listens on these broadcast channels and responds faster than legitimate hosts, effectively poisoning the request and tricking clients into authenticating against the attacker-controlled system
Once the victim initiates an SMB or HTTP authentication, Responder captures the NTLMv2 (or NTLMv1) hashes. These can then be:
- Cracked offline with tools like Hashcat or John the Ripper
- Relayed immediately to pivot to other systems if NTLM signing is not enforced
It’s a simple attack vector, but still very effective in poorly segmented environments where legacy protocols remain enabled. This technique is mapped to MITRE ATT&CK T1557.001 (LLMNR/NBT‑NS poisoning and SMB relay).
Pro tip: Combine with MultiRelay or NTLM relay scripts (part of Impacket) for hands-on pivoting.
Bringing It All Together
While each tool serves a purpose, the real power lies in how they’re used together. That’s why our red team relies on WASP to coordinate, document, and enhance every phase of testing. It’s what allows us to be faster, sharper, and more transparent in every engagement.
For companies seeking to mature their security posture, adopting a platform like WASP, combined with CREST-certified manual testing, is a clear step toward resilience.
Ready to See WASP in Action?
We invite you to try out OP Innovate’s WASP and see how automated, continuous penetration testing can strengthen your security posture.
Contact us for a demo, or get started now by creating your FREE account.