CVE-2025-3648, dubbed “Count(er) Strike”, is a high-severity vulnerability (CVSS 8.2) in ServiceNow’s Now Platform, discovered by Varonis Threat Labs. The flaw allows both authenticated and unauthenticated users to infer sensitive data via crafted range queries when certain Access Control List (ACL) configurations are misapplied.
The vulnerability stems from insufficient granularity in ServiceNow’s ACL logic. Even if users fail restrictive ACL conditions, the platform may leak record counts—providing enough clues for attackers to enumerate confidential dataone condition or character at a time.
- Affected Product: ServiceNow Now Platform
- Patched Versions: Fixes delivered in September 2024, March 2025, and a security update in May 2025
- Public Disclosure: July 8, 2025
- CVSS 4.0 Score: 8.2 (High)
Technical Analysis
Root Cause: ACL Evaluation Logic Flaw
ServiceNow uses four ACL conditions to determine access:
- Roles
- Security Attributes
- Data Conditions
- Script Conditions
In vulnerable configurations, if a user passes any one ACL, access may be granted, even if the others fail. Most critically, failing the last two (data/script conditions) still returns record counts in the UI.
Exploitation Method
Attackers can infer table contents using filter queries like STARTSWITH, CONTAINS, !=, etc. By automating requests with different filters and observing the record count response, attackers can reconstruct sensitive field values character by character.
Example enumeration query:
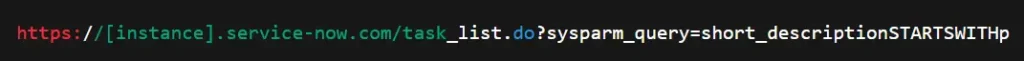
Even low-privileged users or self-registered anonymous accounts can perform this attack if they have access to any misconfigured table.
Impact
- Data Exposure: Credentials, PII, internal configuration data
- Inference Attacks: Extracting sensitive records without direct access
- Low Barrier to Entry: No need for privilege escalation or code execution
- Wide Reach: Potentially affects all ServiceNow instances, including Fortune 500 companies
Mitigation and Remediation
To address the Count(er) Strike vulnerability (CVE-2025-3648), ServiceNow issued a series of security updates aimed at hardening ACL configurations. The first patches were delivered in September 2024 and March 2025, with a more targeted update rolled out in May 2025, specifically designed to help organizations tighten access control logic and reduce the risk of inference-based attacks.
Alongside these patches, ServiceNow introduced several new access control mechanisms, including:
- Deny-Unless ACLs: Require that all ACL conditions are met before access is granted, closing loopholes that previously allowed partial access.
- Query ACLs: Restrict the use of range-based queries (STARTSWITH, CONTAINS, etc.) that can be exploited for data enumeration.
- Security Data Filters: Hide record counts and suppress UI indicators that may leak sensitive information, even when access is denied.
Organizations using ServiceNow are strongly advised to take proactive steps to secure their environments. This includes conducting a thorough audit of all ACL configurations, with particular attention to any tables governed solely by data or script conditions, which are the most vulnerable.
Admins should also disable or limit anonymous and self-registered user access, as these accounts can serve as entry points for exploitation.
Where applicable, teams should implement the new Query ACLs and Deny-Unless rules across sensitive tables to enforce stricter access criteria.
For detailed guidance on securing your instance, ServiceNow has published several knowledge base articles, including:
These resources provide step-by-step instructions for applying the new ACL frameworks and help ensure that access controls are properly configured to mitigate this vulnerability.
ATT&CK & CAPEC Mapping
- MITRE ATT&CK:
- T1574.010 – Services File Permissions Weakness (related technique)
- CAPEC:
- CAPEC-1 – Accessing Functionality Not Properly Constrained by ACLs
OP Innovate Notes
This vulnerability reflects a broader challenge in access control complexity particularly in enterprise platforms where automation and configuration sprawl can unintentionally create weak points.
Despite its technical simplicity, CVE-2025-3648 is a potent data leakage vector. It reinforces the need for continuous validation of access policies, particularly where UI elements like record counts or filtered query results can be used for inference.
Organizations using ServiceNow should treat this as both a patching and architectural issue, prioritizing ACL auditsand implementing the new safeguards to close this enumeration channel.
Need help reviewing your ServiceNow instance or auditing misconfigured ACLs? OP Innovate is ready to support you.
Stay Safe, Stay Secure
OP Innovate Research Team



