A high-severity vulnerability, CVE-2024-4439, has been discovered in the WordPress core, specifically within the Avatar block, affecting versions up to 6.5.2. This stored Cross-Site Scripting (XSS) issue could allow both authenticated and unauthenticated attackers to execute malicious scripts, potentially leading to full site control. Given WordPress’s status as the most widely used CMS globally, the impact and reach of this vulnerability are extensive.
Vulnerability Details
- Affected Component: Avatar block in WordPress
- Affected Versions: Up to 6.5.2
- Vulnerability Type: Stored Cross-Site Scripting (XSS)
- CVE-ID: CVE-2024-4439
- Severity Rating: 7.2 (High) on the CVSS scale
- Discovery: The flaw results from inadequate output escaping of user display names, where malicious scripts are injected and executed.
- Affected Code Snippet:
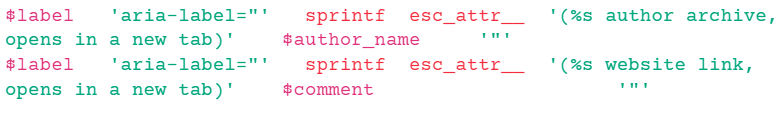
This code illustrates the improper sequencing of esc_attr() and sprintf() functions, leading to insufficient escaping of user-supplied data. This oversight allows the injection of XSS payloads into WordPress sites via user display names.
Exploitation and Impact
- Exploitation: Can be exploited by both logged-in users (with at least contributor access) and unauthenticated visitors on pages displaying comment authors’ avatars.
- Potential Impact: Enables attackers to inject arbitrary web scripts into pages, add administrative accounts, modify site content, inject backdoors, and more, potentially compromising the entire website.
Mitigation and Remediation
- Immediate Update Required: WordPress has released a security update in version 6.5.2 on April 9, 2024, which resolves this vulnerability. This patch is also backported to earlier versions starting from 6.1.
- Recommended Actions:
- Ensure that all WordPress installations are updated to version 6.5.2 or later.
- Conduct site audits to check for signs of compromise or unauthorized changes.
- Regularly update all components of the WordPress ecosystem, including themes and plugins.
Recommendations for Site Administrators
- Vigilance: Monitor and review all site activities and user roles, especially new administrative users or unusual content changes.
- Security Practices: Employ comprehensive security solutions, including Web Application Firewalls (WAFs) and regular security scanning.



