The Open Web Application Security Project (OWASP) has released an updated OWASP Top 10 list for the first time in four years.
This list is a global standard highlighting the most critical risks to web applications, and reveals that while new threats are emerging, many of the same fundamental vulnerabilities continue to plague applications.
For cybersecurity practitioners and decision-makers, the updated OWASP Top 10 (2025 release candidate) offers both a wake-up call and a roadmap for where to focus web application security efforts.
The Updated OWASP Top 10 at a Glance
Unveiled at OWASP’s Global AppSec conference in November 2025, the new Top 10 ranks today’s most pressing web application security concerns. The categories on the updated list are as follows:
- Broken Access Control: (Still the #1 risk, involving failures to enforce user permissions and access levels)
- Security Misconfiguration: (Incorrect or insecure configuration of systems or cloud services)
- Software Supply Chain Failures: (Compromises in the processes and components that build and update software)
- Cryptographic Failures: (Weak or missing cryptography leading to exposure of sensitive data)
- Injection: (Flaws that allow attackers to inject malicious code/commands, e.g. SQL injection, XSS)
- Insecure Design: (Security weaknesses from design flaws or lack of security controls in design)
- Authentication Failures: (Broken user authentication or session management)
- Software or Data Integrity Failures: (Integrity violations in software systems or data, e.g. tampering)
- Logging and Alerting Failures: (Inadequate logging/monitoring to detect and respond to incidents)
- Mishandling of Exceptional Conditions: (New category for improper error and exception handling)

The list features many familiar issues from the 2021 Top 10, with a few notable changes and additions. Notably, Server-Side Request Forgery (SSRF), which was #10 in the previous 2021 list, no longer appears as its own category. It has been rolled into the Broken Access Control category.
Two new entries have arrived: Software Supply Chain Failures (a new category that subsumes the old “Vulnerable and Outdated Components” issue from 2021 and Mishandling of Exceptional Conditions (making the Top 10 for the first time, covering weaknesses in error handling, such as improper exception management or “fail open” scenarios.
Old Vulnerabilities Still Dominate
A takeaway from the updated OWASP Top 10 is how many long-standing vulnerabilities remain widespread.
Broken Access Control Remains #1
Broken Access Control retains the top spot as the most critical web app risk, just as it was in 2021. This category includes things like missing or ineffective permission checks, allowing attackers to act outside their intended privileges.
OWASP’s data shows that about 3.7% of applications tested had one or more known weaknesses in access control and by some measures, virtually every application tested had at least some form of broken access control issue.
This is an astonishing reality: even after years of security improvements, Broken Access Control is “hands down” the #1 vulnerability category for web apps and APIs. Common pitfalls include things like not enforcing role-based access, predictable URLs allowing unauthorized access, or failures to validate user privileges.
Misconfigurations Surge to #2
Other familiar threat categories also continue to impact applications. Security Misconfiguration, for example, has surged from a mid-list position to now ranking as the #2 risk. This rise reflects the ongoing issues companies face in securely configuring their applications and infrastructure.
Misconfigurations can range from leaving default credentials or sample files in production, to cloud storage buckets inadvertently left open to the public. Such mistakes are both common and dangerous. OWASP presenters noted that leaked cloud credentials and other misconfigurations are the top cloud security issue, often implicated in breaches.
As systems grow more complex (especially in cloud and containerized environments), the potential for configuration errors has grown as well.
Familiar But Persistent Threats
Meanwhile, Injection flaws (like SQL injection and cross-site scripting) and Cryptographic Failures (weak or misused encryption) remain on the Top 10, though they have dropped in rank compared to four years ago. Injection, which was the #1 issue in 2017 and #3 in 2021, is now #5, an indication that industry practices like parameterized queries, input validation frameworks, and automated scanning have helped reduce (but not eliminate) these vulnerabilities.
Cryptographic failures, such as using weak algorithms or poor key management, dropped from #2 to #4. These drops are encouraging signs that awareness and better tooling (e.g. integrating strong encryption libraries and enforcing their use) may be having an effect.
Insecure Design, a category added in 2021 to spotlight flaws stemming from design decisions, also fell in rank (#6 now, from #4 in 2021). OWASP notes that this improvement may be driven by increased use of threat modeling and “secure by design” initiatives during development.
It’s important to realize, however, that dropping in rank doesn’t mean a risk has vanished. Injection and cryptographic issues still exist in many applications, and they can lead to severe breaches if not addressed. The Top 10 is a relative ranking; even lower-ranked items can be prevalent.
New and Rising Threats: Supply Chain and Exception Handling
While many Top 10 entries will sound familiar to veteran security professionals, the 2025 update also introduces new focus areas that mirror the evolving threat landscape.
Software Supply Chain Failures (#3)
One of the most impactful additions is Software Supply Chain Failures at the #3 spot. This category was added to acknowledge the growing risk posed by vulnerabilities in the software pipeline itself.
According to OWASP’s definition, supply chain failures refer to breakdowns or compromises in the process of building, deploying, or updating software, often caused by issues in third-party code, open-source libraries, build tools, or other dependencies that applications rely on.
In essence, even if your own code is secure, a weakness in a component you use (or a malicious injection into your build process) can undermine your application. High-profile incidents in recent years drive this point home, from exploited open-source library vulnerabilities (like the Log4j flaw) to sophisticated attacks inserting backdoors into trusted software updates (as seen in the SolarWinds breach).
Mishandling of Exceptional Conditions (#10)
Another new entrant on the list is Mishandling of Exceptional Conditions, landing at #10. This mouthful of a category essentially covers weaknesses in how applications handle errors, exceptions, and unexpected situations.
For instance, if an application “fails open” (granting access or leaving data exposed when an error occurs) or if it reveals sensitive debugging information in error messages, those are examples of mishandled exceptions that can be leveraged by attackers.
This category has been on OWASP’s radar for some time. It hovered just outside the Top 10 in previous data, and now there is enough data and community concern to push it into the official list.
Developers and testers should ensure that the application behaves securely even when things go wrong: errors should be logged in detail for internal teams, but generic and safe for users.
Reclassification: SSRF and Other Refinements
OWASP’s update also involved reclassifying certain risks rather than simply adding and removing. We already noted that SSRF (Server-Side Request Forgery), a prominent new issue in 2021’s Top 10, is no longer listed separately.
OWASP decided to merge SSRF into Broken Access Control, suggesting that SSRF vulnerabilities (where an application can be tricked into fetching unauthorized internal resources or external URLs) fundamentally boil down to access control issues (the application is accessing something it shouldn’t).
This doesn’t mean SSRF is any less dangerous; rather, it reflects an effort to simplify the categories. Practitioners should still be testing for SSRF scenarios (for example, manipulating URLs that server-side code fetches) as diligently as ever, even though it won’t show up as its own line item on the Top 10.
Beyond SSRF, the Top 10 list names have been tweaked in a few places (e.g. “Identification and Authentication Failures” is shortened to Authentication Failures, and “Security Logging and Monitoring Failures” is now Logging and Alerting Failures. These are largely semantic updates to clarify scope.
The core concerns remain similar: authentication failures cover issues like weak password handling, missing authentication for critical functions, or flawed session management, while logging/alerting failures mean not recording important events or lacking proper alerting to respond to incidents.
Main Takeaway
For organizations, the takeaway is that the same categories of weaknesses that have led to breaches for the past decade are still very much in play, and attackers will exploit whichever gap is left open, whether it’s an unpatched library (supply chain issue), an overly verbose error response (exception handling issue), or an old classic like SQL injection.
Strengthening Your Web App Security with OP Innovate’s WASP Platform
Keeping up with the OWASP Top 10 and the myriad of other threats beyond it can be challenging. That’s where OP Innovate can help. OP Innovate specializes in web application penetration testing, and we’ve built our own platform called WASP (Web Application Security Platform) to make this process smarter and more effective.
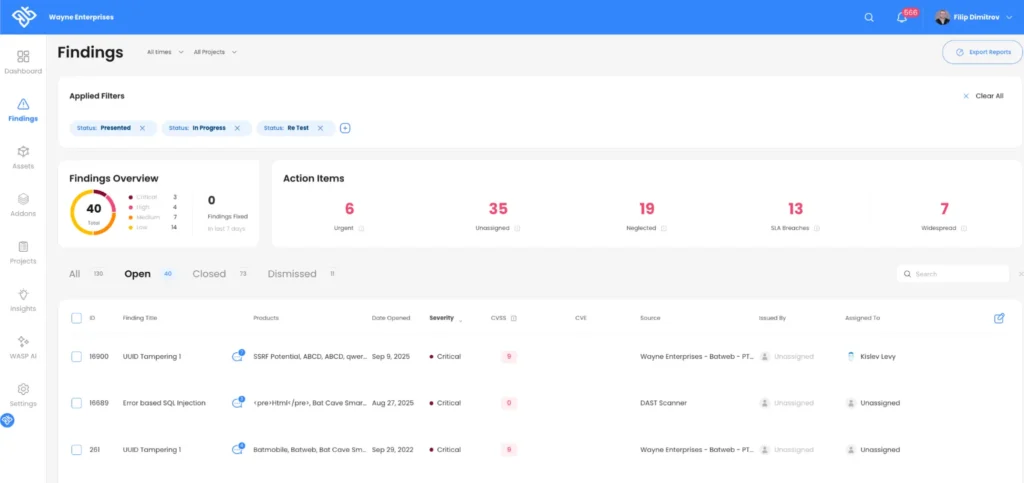
The “Findings” dashboard in WASP, revealing your application risks
WASP combines automated scanning (covering common OWASP Top 10 issues like injections, misconfigurations, and known vulnerabilities) with continuous manual expertise from our elite team of ethical hackers. This hybrid approach means you get the best of both worlds: the speed of automation and the savvy of human-led testing, delivered as an ongoing service.
With WASP, our team can continuously validates your web application security, not just with one-off tests every year, but through ongoing assessments that keep pace with your development.
As new vulnerabilities emerge (for instance, a newly disclosed supply chain flaw or a fresh zero-day in a popular framework), our platform and experts are on hand to identify if your applications are at risk.
We help you prioritize and remediate findings quickly, with integration into your development workflow (such as Jira ticketing) to streamline the fix process. The result? You reduce exposure time and catch issues before they can be exploited, strengthening your security posture against the very risks highlighted in OWASP’s Top 10.
Ready to take your web application security to the next level? Get in touch with OP Innovate for a demo of the WASP platform or to discuss a penetration testing engagement tailored to your needs.










