The Burp Suite AI Reporter Plugin is designed to eliminate the repetitive, time-consuming aspects of vulnerability documentation, allowing cyber researchers to dedicate their expertise to in-depth security analysis. By significantly reducing the reporting burden, security teams can focus more on testing applications, identifying critical weaknesses, and strengthening defenses.
TL;DR:
The Burp AI Reporter automates vulnerability reporting, allowing security researchers to focus on finding issues rather than writing reports. Integrated with OP Innovate’s WASP, it ensures efficient, accurate, and privacy-conscious documentation. The AI-driven process reduces manual effort by up to 60%, generating full reports within seconds.
🔹 Optimized research time – Less time on documentation, more time on security research.
🔹 Seamless integration – Works directly with OP Innovate’s WASP PTaas.
🔹 Fast & structured reports – AI fills in details like descriptions, risk assessment, CWE mapping, and mitigations.
🔹Clear & actionable insights – Developers receive well-structured reports with precise mitigation steps, making it easier to fix vulnerabilities efficiently.
Introduction
Burp Suite is a widely used tool among penetration testers, security researchers, and red teamers for assessing the security of web applications. It provides a comprehensive set of features, including traffic interception, scanning, fuzzing, and automation capabilities, making it an essential part of any security professional’s toolkit. While its capabilities are powerful, reporting remains one of the most time-consuming aspects of security research.
Security professionals often spend hours documenting vulnerabilities, writing detailed descriptions, reproducing steps, and providing remediation guidance. This process is tedious, prone to human error, and takes away valuable time that could be spent on deeper analysis and testing.
Manually extracting relevant data, structuring findings, and compiling reports in a clear, standardized format leads to inefficiencies, inconsistencies, and delays in delivering actionable insights to stakeholders.
To address this challenge, our team has developed a Burp Suite plugin that harnesses AI to automate the reporting process. This solution enables security professionals to generate structured, high-quality vulnerability reports directly within Burp Suite, significantly reducing manual effort and streamlining workflow.
Anonymization & Data Privacy
One of the primary concerns when automating security reporting is ensuring that sensitive client data remains protected. The Burp AI Reporter Plugin is built with complete anonymization in mind, ensuring that:
- No personally identifiable information (PII) or client-specific details are stored or transmitted.
- Findings are processed within a secure, isolated environment.
- Reports are generated following strict security and compliance guidelines.
This level of privacy ensures that organizations can trust the tool to automate their workflow without introducing additional security risks.
Seamless Integration with OP Innovate’s WASP
The Burp Suite AI Reporter is fully integrated with OP Innovate’s Web Application Security Platform (WASP), enabling a streamlined workflow from vulnerability discovery to remediation. WASP provides an organized framework for managing security assessments, tracking vulnerabilities, and ensuring rapid response times.
By connecting Burp AI Reporter with WASP, security teams can:
- Automatically push findings into WASP’s centralized vulnerability management system.
- Maintain a structured repository of security issues.
- Generate standardized reports that align with industry best practices.
How Does It Work?
- A researcher identifies a vulnerability within Burp Suite.
- The vulnerable request is sent to the Burp AI Reporter Plugin.
- The researcher provides brief input on the vulnerability.
- The AI processes the details, adhering to a predefined reporting template.
- Within seconds, a well-structured report is generated, including:
- Vulnerability Description
- Steps to Reproduce
- Risk Assessment
- CWE Mapping
- Mitigation Recommendations
- The researcher integrates with WASP and upload the findings into the system
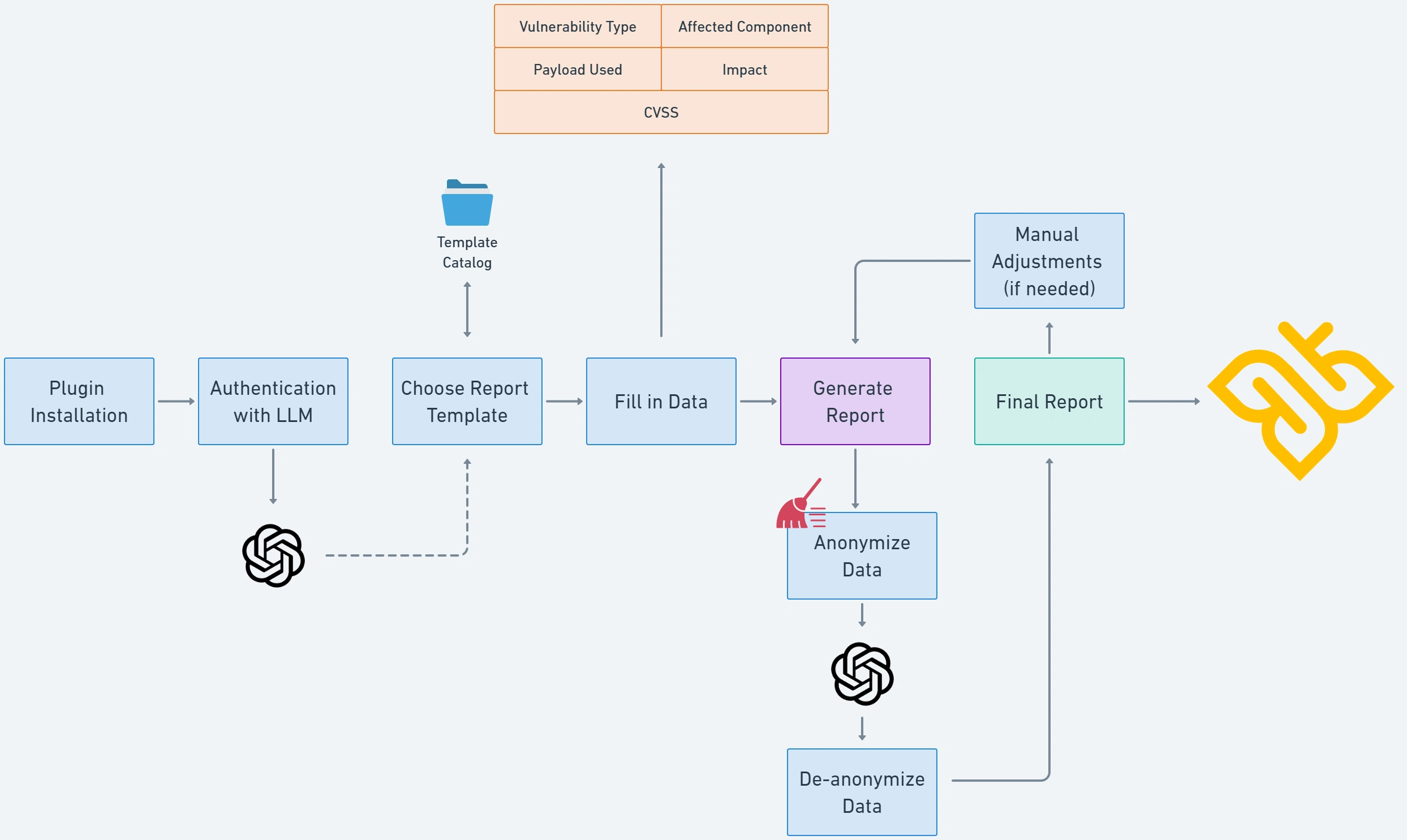
This automated process eliminates the need for manual report formatting and content structuring, empowering security researchers to operate more efficiently.
Conclusion
The Burp AI Reporter Plugin is a game-changer for security teams looking to enhance productivity without compromising quality. By leveraging AI to automate the reporting process, organizations can improve efficiency, maintain consistency, and ensure rapid documentation of security findings.
With seamless integration into OP Innovate’s WASP, robust anonymization measures, and an intuitive workflow, Burp AI Reporter is set to redefine how security research teams handle vulnerability reporting.
Try Burp AI Reporter today and experience the next level of automated security reporting!
Don’t waste your budget on reports – invest in real security. When choosing your next penetration testing team, ensure your resources are spent where they matter most—on deep, expert-driven security research, not excessive documentation.
Many teams waste time on documentation instead of testing. OP Innovate prioritizes real security, using tools like Burp AI Reporter to automate reporting and focus on real threats. Get more value from your penetration test with OP Innovate.
- Credits
- Special thanks to Dan Shallom and Nicole Sheinin Levi, top contributors who played a crucial role in the development and refinement of Burp AI Reporter.
- This plugin was developed over several months of hard work and dedication.









