How an Iranian-Linked Group Turned Simple Security Weaknesses into Mass Breaches
By Matan Matalon, Filip Dimitrov
The digital frontlines of the Israel-Gaza conflict have rapidly evolved into an active and persistent cyber battlefield. Over the past year, multiple pro-Palestinian threat groups, including Handala and Cyber Toufan, have launched coordinated campaigns targeting Israeli organizations.
These attacks go beyond typical cybercrime; they are politically motivated operations designed to disrupt, destabilize, and damage. Since late 2023, Cyber Toufan (Arabic for “cyber storm”) has claimed responsibility for over 100 breaches across sectors including government, defense, finance, and critical infrastructure.
Over the past months, the OP Innovate Incident Response (IR) team has investigated three confirmed Cyber Toufan intrusions.
Each case followed a consistent pattern: initial access via weak or reused credentials without MFA, stealthy lateral movement across the network, and coordinated data leak campaigns distributed publicly via Telegram. Unlike traditional APTs that rely on sophisticated zero-days, these actors exploit poor security hygiene, turning basic negligence into their primary attack vector.
In this post, we will cover:
- The types of organizations typically targeted by Cyber Toufan
- Key findings and TTPs from real-world investigations by OP Innovate
- How the group’s behavior maps to the MITRE ATT&CK framework
- Strategic recommendations to strengthen your defenses against similar threats.
Who Does Cyber Toufan Target?
Cyber Toufan’s self-proclaimed ideology is rooted in the Israel-Gaza conflict. Its very name (“storm”) signals ideological motivations aligned with regional tensions. Public statements and behavioral analysis indicate that the group’s objective is not financial gain, but political and psychological disruption aimed at damaging reputations, eroding trust, and generating public pressure through widespread data leaks.
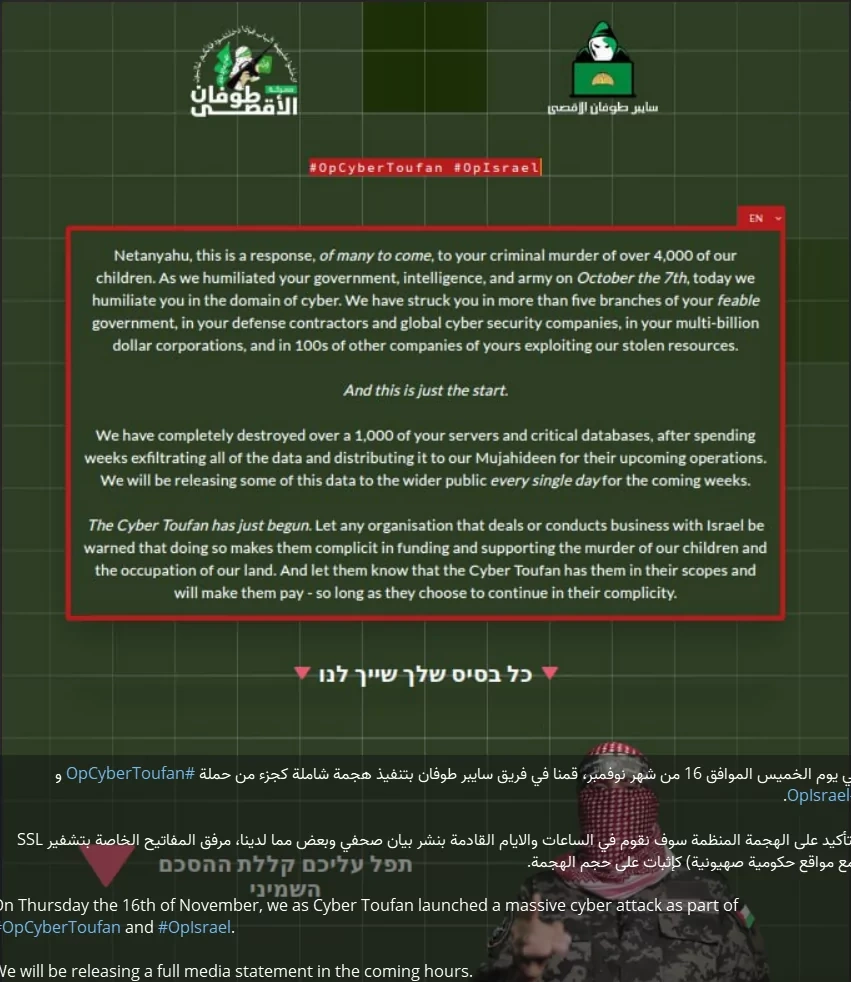
Cyber Toufan’s first Telegram post, explaining their goals (November, 2023)
In practice, the group leaks stolen data via Telegram and dedicated leak sites. These leaks are timed to maximize attention and impact, often released days or even weeks after the initial breach.
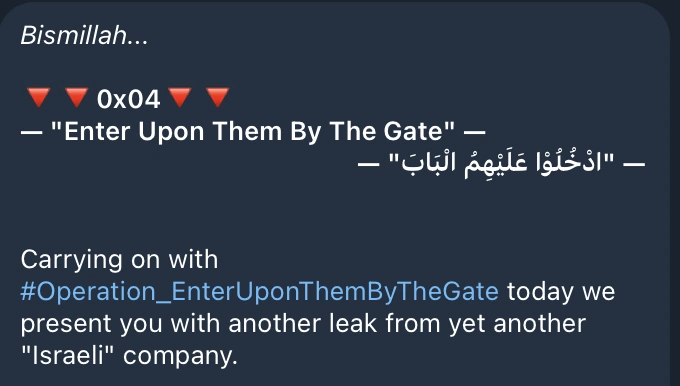
Cyber Toufan announcing a new company leak on Telegram
The attack pattern shows a clear focus on entities tied to Israel’s economy and security, rather than on opportunistic or global targets. Public reports and OP Innovate’s own investigations confirm that many of Cyber Toufan’s victims include government contractors, tech firms, infrastructure providers, and international companies doing business in Israel. Each organization targeted has had a direct or indirect connection to Israeli projects or institutions.
An emerging trend observed across multiple incidents is Cyber Toufan’s focus on organizations whose VPN or firewall infrastructure is managed by third-party service providers (e.g., Bezeq, Partner). In these cases, attackers appear to exploit default or previously leaked credentials associated with the service provider’s configurations – gaining access not by breaking in, but by walking through an unlocked door.
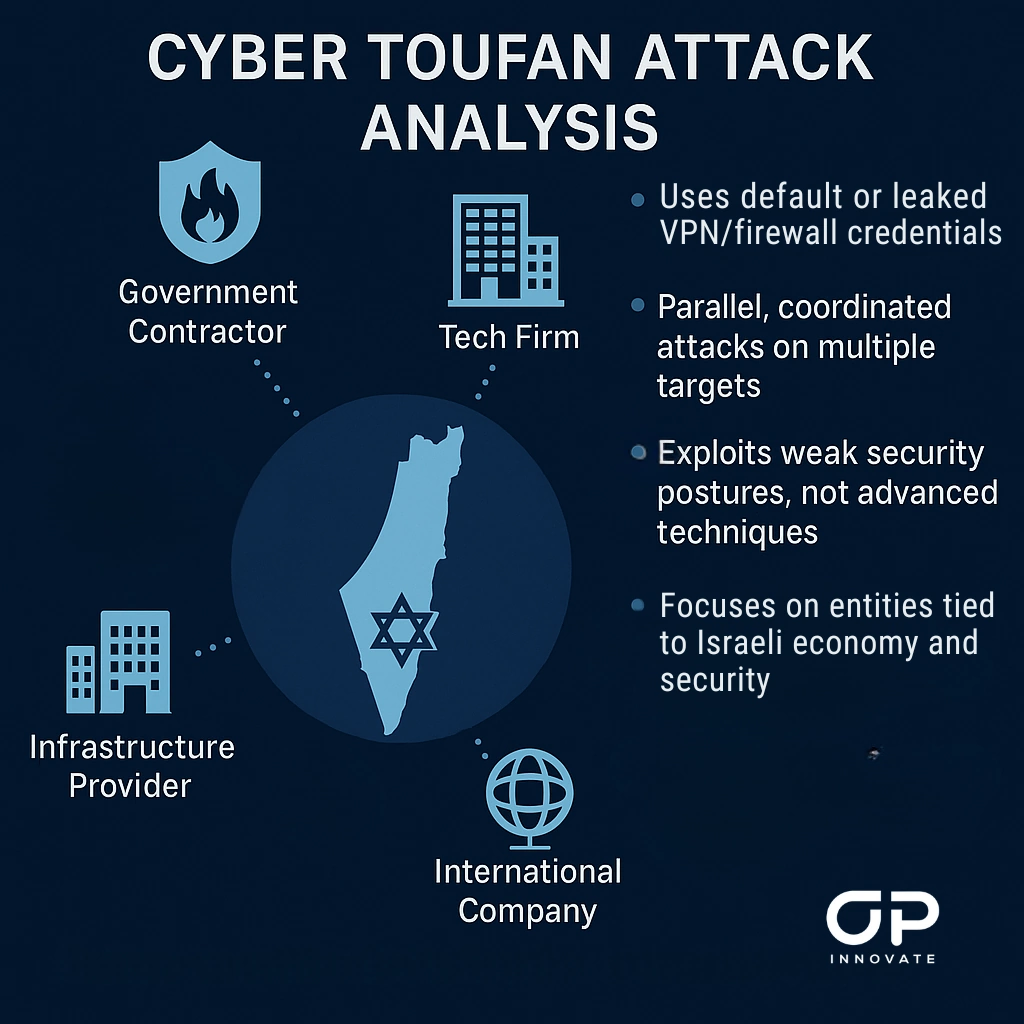
Moreover, forensic evidence indicates that these attacks were often executed in parallel, suggesting a coordinated campaign aimed at breaching multiple targets simultaneously. This strategy likely allowed the group to collect a large volume of sensitive data in a short time frame, which was then selectively leaked at later stages for strategic or propagandist purposes.
Critically, in every case OP Innovate investigated, the attackers didn’t need to rely on sophisticated malware or zero-day exploits. Instead, they exploited weak security postures – missing MFA, open ports, default accounts, and flat networks. Cyber Toufan doesn’t have to be advanced when its targets are unprepared.
Tactics, Techniques and Procedures (TTPs)
Cyber Toufan’s confirmed TTPs blend hacktivist methods with advanced intrusion techniques. Analysis of the incidents and OSINT indicates:
Reconnaissance
Cyber Toufan actively maps the external surfaces of potential targets to identify weak entry points (MITRE T1595). Their reconnaissance efforts include:
- Gathering information on the organization’s external attack surface – including exposed servers, firewall interfaces, VPN admin panels, and remote access points – often focusing on organizations that rely on managed VPN/firewall services provided by third-party vendors (e.g., Bezeq, Partner). These setups are frequently targeted due to reused, default, or leaked credentials left unmonitored.
- Hunting for leaked or stolen credentials – collected from infostealer logs, previous breaches, or credential marketplaces, with an emphasis on low-friction, stealthy access routes.
- Detecting the presence or absence of basic security controls – such as multi-factor authentication (MFA), to assess whether compromised credentials can be reused without triggering alerts.
These methods reflect a deliberate preference for exploiting misconfigurations and neglected hygiene over deploying advanced tooling. In multiple incidents investigated by OP Innovate, evidence pointed to early scanning and targeting of externally managed VPN appliances and weak authentication practices as the initial vectors.
Resource Development & Initial Access
Cyber Toufan prepares and maintains infrastructure to support its operations (MITRE TA0042), and gains entry primarily through credential abuse and misconfigured remote access points (MITRE TA0001).
Their tactics include:
- Setting up attacker-controlled infrastructure, such as rented VPS servers or VPN endpoints, to anonymize operations and manage stolen data (MITRE T1583 – Acquire Infrastructure).
- Using valid credentials to access exposed VPN or RDP services, often exploiting reused, default, or leaked login data tied to externally managed firewall/VPN platforms (MITRE T1078 – Valid Accounts).
In several OP Innovate cases, access was obtained without malware or brute-force techniques—just unmonitored, legitimate login paths.
Execution & Lateral Movement
Once inside the network, Cyber Toufan leverages native tools to navigate laterally and exfiltrate data without triggering alarms (MITRE TA0002, TA0008).
Their tactics include:
- Scanning the internal network after gaining an internal IP to locate machines with exposed and unprotected SMB shares, often configured with no password enforcement or weak credentials. These misconfigurations allow the attackers to access and pull files without needing to compromise endpoints directly.
- Using living-off-the-land techniques, such as PowerShell, PsExec, and native Windows file-sharing protocols (e.g., SMB), to move laterally and collect data while blending in with normal system activity (MITRE T1021.002 – SMB/Windows Admin Shares).
In every case investigated by OP Innovate, no malware was observed. The attackers relied on credential-based access, poorly secured file-sharing configurations, and legitimate tools to remain undetected throughout the intrusion.
Defense Evasion
Cyber Toufan places a strong emphasis on remaining undetected, using subtle techniques to avoid raising alarms during and after their intrusions (MITRE TA0005).
Their tactics include:
- Leveraging existing administrative permissions and built-in system tools, rather than deploying custom malware or external binaries, reducing their digital footprint and avoiding antivirus triggers.
- Maintaining low operational noise, with no excessive scanning or privilege escalation attempts, helping them blend into the background of day-to-day network activity.
- Taking advantage of insufficient endpoint visibility and lack of real-time alerting, which prevents defenders from correlating or identifying suspicious lateral movement or access patterns.
- Exploiting fragmented or missing log coverage across systems, which hampers both real-time detection and post-incident forensic analysis (MITRE T1027 – Obfuscated Files or Information, MITRE T1562 – Impair Defenses).
This quiet, methodical approach enables Cyber Toufan to persist in compromised environments long enough to extract high-value data—often without being discovered until the information is publicly leaked.
Exfiltration & Impact
Cyber Toufan’s endgame is not only data theft, but also reputational and operational damage – executed in phases designed for maximum psychological and strategic effect (MITRE TA0010, TA0040).
Their tactics include:
- Extracting sensitive files via SMB or remote admin tools, often staging the data for exfiltration in compressed archives and transferring it over encrypted channels (MITRE T1041 – Exfiltration Over C2 Channel).
- Coordinating large-scale exfiltration across multiple victims in a short timeframe, suggesting an intentional effort to maximize intelligence collection before exposure.
- Delaying the publication of stolen data, often leaking it days or weeks later via Telegram or dedicated leak sites, likely to coincide with strategic events or media cycles.
MITRE ATT&CK Mapping
| Tactic | Technique (ID) | Evidence from OP Innovate IR Reports |
| Reconnaissance (TA0043) | Active Scanning (T1595) | Scanning for exposed VPNs, firewall interfaces, and remote access points to identify weak entry vectors. |
| Reconnaissance (TA0043) | Gather Victim Identity Information (T1589) | Identifying stolen credentials and checking for MFA to assess potential for silent reuse. |
| Resource Development (TA0042) | Acquire Infrastructure (T1583) | Setting up attacker-controlled infrastructure (e.g., VPS, VPN) to support operations. |
| Initial Access (TA0001) | Valid Accounts (T1078) | Using stolen, reused, or default credentials to gain initial access to exposed remote services. |
| Execution (TA0002) | Windows Admin Shares (T1021.002) | Executing commands using built-in tools like PowerShell or PsExec on remote systems via SMB. |
| Lateral Movement (TA0008) | Windows Admin Shares (T1021.002) | Moving laterally within the network using poorly secured SMB shares and native Windows protocols. |
| Defense Evasion (TA0005) | Obfuscated Files or Information (T1027), Impair Defenses (T1562) | Avoiding detection by leveraging built-in tools, avoiding malware, and exploiting insufficient logging. |
| Exfiltration (TA0010) | Exfiltration Over C2 Channel (T1041) | Transferring stolen data over encrypted channels, often after staging and compressing it internally. |
| Impact (TA0040) | Strategic Leak Timing (mapped to TA0040 without specific technique ID) | Delaying public leaks of stolen data to maximize reputational impact and align with media or strategic timing. |
Cyber Toufan’s Digital Footprint
Based on the known breaches and leak activity, key infrastructure and behavioral markers include:
| Category | Details |
| Domains / URLs | toufanleaks.org (official leak portal)Gofile download links (e.g. gofile.io/d/HXPvCq with password CyberToufan) Telegram analytics links from tgstat.com. |
| Threat Actor Handles | Telegram channels: t.me/CyberToufant.me and CyberToufanBackup |
| Tools & Payloads | No unique malware has been publicly attributed. However, defenders should monitor for atypical use of legitimate admin tools such as PowerShell, remote desktop sessions from unknown sources, or SMB enumeration; all patterns seen across our IR cases. |
The Real Problem: No Logs, No Segmentation
Cyber Toufan didn’t breach these environments using zero-days or sophisticated malware. In all three incidents we were engaged in, the intrusions succeeded because basic cybersecurity hygiene was missing, allowing the attackers to walk in, pivot freely, and exfiltrate sensitive data without resistance.
No centralized logging: In one case, VPN logs were retained for just a single day, so by the time the IR team was engaged, there was no record of how access was gained. This wasn’t an isolated failure: across all cases, we saw missing or incomplete audit trails, which made it nearly impossible to trace the attack paths.
With basic logging in place, the organizations could have caught unusual VPN logins, lateral movement, or early-stage reconnaissance. Instead, those red flags went unnoticed.
Find out more about the importance of logging:

No segmentation, no access controls: In multiple cases, attackers encountered flat internal networks and unprotected SMB file shares. One file server had a guest account with no password (no authentication required to access sensitive project files).
Once inside, the attackers didn’t need to escalate privileges or bypass endpoint protections as everything was already open.
How to Protect Yourself
Unfortunately, many mid-sized, or even larger businesses still operate with minimal security controls, opening the door for groups like Cyber Toufan to exploit basic vulnerabilities or misconfigurations that should’ve never been allowed to exist.
Here are our top recommendations for organizations looking to protect themselves against these targeted attacks:
- Enforce MFA everywhere
Especially on VPNs, Remote Desktop Tools, and email platforms. Credentials will be stolen, but MFA will stop them from being used.
If you want to stay in the know about leaked or stolen credentials, OP Innovate’s WASP platform includes a credential scanner that continuously monitors for exposed usernames and passwords, alerting your team the moment your organization is at risk.
- Eliminate default and dormant accounts
Generic usernames like “admin” or “user1” are easy targets. If they’re not in use, disable them. If they are, rename and monitor them closely.
- Segment your network
Flat networks are a gift to attackers. Segment by function or department, and enforce strict firewall rules between zones.
- Lock down file servers
Disable guest accounts. Apply least-privilege access policies. Regularly audit who has access to what.
- Centralize logging and extend retention
Invest in a SIEM or logging solution that aggregates logs from VPNs, firewalls, and endpoints. Keep those logs for at least 90 days.
Stay Ahead of Threats with OP Innovate
As threats continue to evolve, the need for actionable intelligence and expert intervention has never been greater. OP Innovate is at the forefront of the fight against sophisticated threat actors like Cyber Toufan by actively supporting organizations with rapid incident response (IR) and cutting-edge threat intelligence.
With our WASP platform, organizations can proactively identify and remediate vulnerabilities that groups like Cyber Toufan actively seek to exploit. WASP combines continuous manual and automated penetration testing with real-time reporting to help organizations detect weaknesses before attackers do.
Contact us today to learn how OP Innovate can help safeguard your business from emerging cyber threats.
We regularly publish blog and Cyber Threat Intelligence (CTI) updates on our website. Sign up to receive our latest updates straight to your inbox.