Penetration testing platforms are a great way to centralize vulnerability discovery and triage. However, when evaluating penetration testing platforms, many organizations make the mistake of prioritizing flashy dashboards or automated scan results. But real security goes deeper. A modern Pentesting-as-a-Service (PTaaS) platform should deliver far more than basic vulnerability scans.
If you’re in the market for a pentesting platform, here’s what you should be looking for, and how WASP by OP Innovate stands out from the crowd.
Expert Human-Led Testing
Human expertise is essential for building an effective, always-on penetration testing program. Unless you have in-house, professional penetration testers working with the platform, you must look for solutions that combine automated scanning with certified human-led testing to uncover complex vulnerabilities, validate findings, and provide meaningful remediation guidance.
Otherwise, you’re relying entirely on automated scans that miss critical vulnerabilities, lack business context, and will leave you with a false sense of security. Automated tools simply can’t find every flaw; only a skilled tester has the intuition and creativity to root out complex logic errors or chained exploits.
The vendor’s testers should be experienced and certified (e.g. CREST, OSCP). Consistency also matters: a dedicated team that learns your environment will find more than rotating crowdsourced testers. In short, the pentesting service should rely on top-level professionals who go beyond vulnerability scans to actively exploit and verify issues.
- Human-Led Pentesting: Tools with automated “wizards” are useful for baseline checks, but the platform must also offer manual penetration tests by experts. Only hands-on testing can confirm which weaknesses are truly exploitable.
- Certified Testers: Ensure the provider’s team holds high-level qualifications. Certifications like CREST, OSCP. OSCE. OSWE indicate the vendor invests in skilled talent. Avoid models that drop in a random tester each time. You want continuity and deep knowledge of your apps.
- Comprehensive Coverage: Look for a platform that executes a full scope of tests (network, web, API, etc.) as needed. Skilled testers should cover every phase of testing, not just run a canned scan.
How WASP excels: WASP delivers on-demand CREST-certified manual penetration tests in addition to any automated checks. Manual test can be scheduled seamlessly from within the platform according to your specific needs, in just a few clicks.

Contextualized Risk Prioritization
Finding vulnerabilities is one thing, but knowing which ones actually matter is another. Many pentesting tools overwhelm teams with lengthy reports full of unfiltered results, including low-risk issues or false positives that have little impact on your security posture.
For security efforts to be effective, the platform must prioritize vulnerabilities based on severity, exploitability, and business impact. From just a quick look at the finding, you should be able to answer questions like:
- Could this vulnerability be exploited from the internet?
- Does it expose sensitive data or critical infrastructure?
- Is it already being exploited in the wild?
By focusing attention on the most dangerous issues, organizations can reduce mean time to remediation (MTTR) and avoid wasting resources on low-risk issues.
How WASP excels:
WASP automatically triages findings, removing false positives and ranking vulnerabilities based on severity, exploitability, and the business context of your systems. All findings are ranked from “informational” to “Critical,” so users know exactly what to focus on to improve security posture.
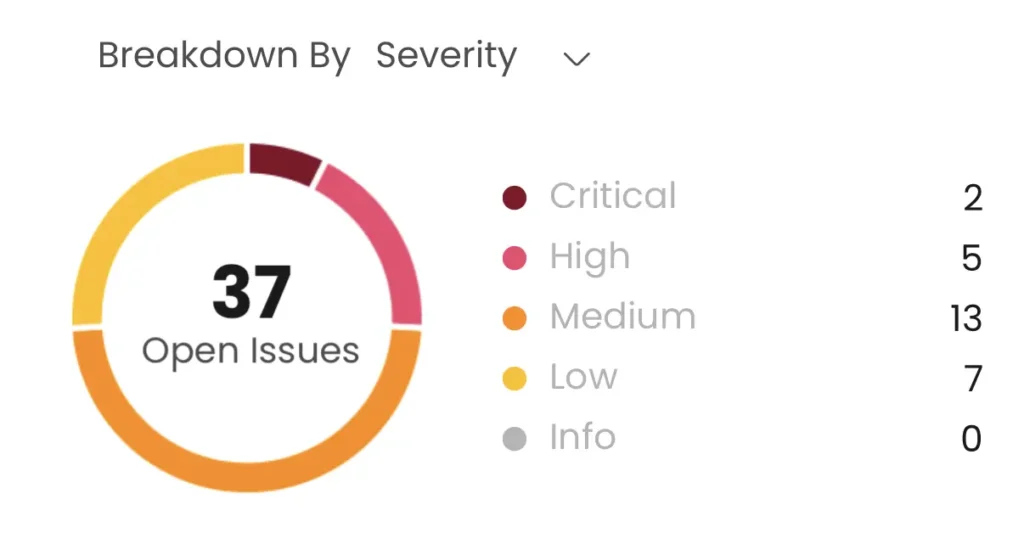
Remediation Guidance
Uncovering vulnerabilities is just the beginning. Fixing them is where real security gains happen. Yet, many pentesting platforms fall short when it comes to remediation. They hand off a report and walk away, leaving internal teams to decipher vague descriptions or incomplete guidance.
A modern PTaaS platform must do more. It should bridge the gap between discovery and resolution, helping developers understand not only what’s broken, but how to fix it effectively, and why it matters.
Look for platforms that:
- Provide clear, actionable remediation steps tailored to each vulnerability and your environment. Generic “patch it” advice isn’t enough.
- Facilitate collaboration between security teams and developers, either through platform-native chat, comments, or guidance from the testing team.
- Offer on-demand retesting, so you can verify whether a fix was successful and close the loop with confidence.
Without remediation support, even high-quality findings risk going unaddressed. Security is a team sport, and your platform should enable that.
How WASP excels:
WASP makes remediation faster, clearer, and collaborative. Every vulnerability comes with detailed mitigation guidance, complete with reproduction steps, business context, and expert commentary. Developers can request clarification or submit fixes for instant retesting directly in the platform with no need to wait weeks for a follow-up engagement.
This model enables teams to resolve issues faster and more confidently, while keeping security teams in the loop at every stage. By turning findings into fixes, WASP closes the gap between testing and action.
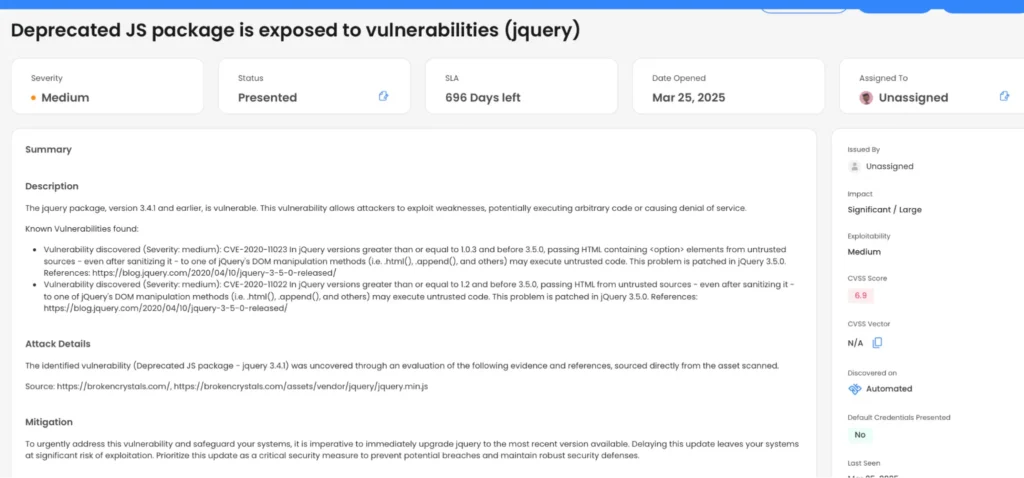
Sample finding report in WASP
Actionable Reporting
A pentesting platform must translate findings into action.
Good reporting is key: it should include both a concise executive summary and a detailed technical breakdown for engineers. Each vulnerability write-up needs impact/risk context, attack vectors and proof-of-concept, plus clear mitigation steps.
In other words, the report should not be a raw dump of data but a prioritized roadmap for fixing issues.
- Concise executive summaries for leadership, highlighting risk posture, business impact, and progress over time.
- Detailed technical breakdowns for engineering teams, including vulnerability descriptions, attack vectors, and proof-of-concept (PoC) evidence like screenshots or payloads.
- Customizable, exportable formats to support internal workflows, board reporting, or audit requirements.
How WASP excels: WASP provides one-click custom reports for managers and auditors, combining business-friendly summaries with full technical detail. Its output includes all the proofs-of-concept and remediation advice you need.
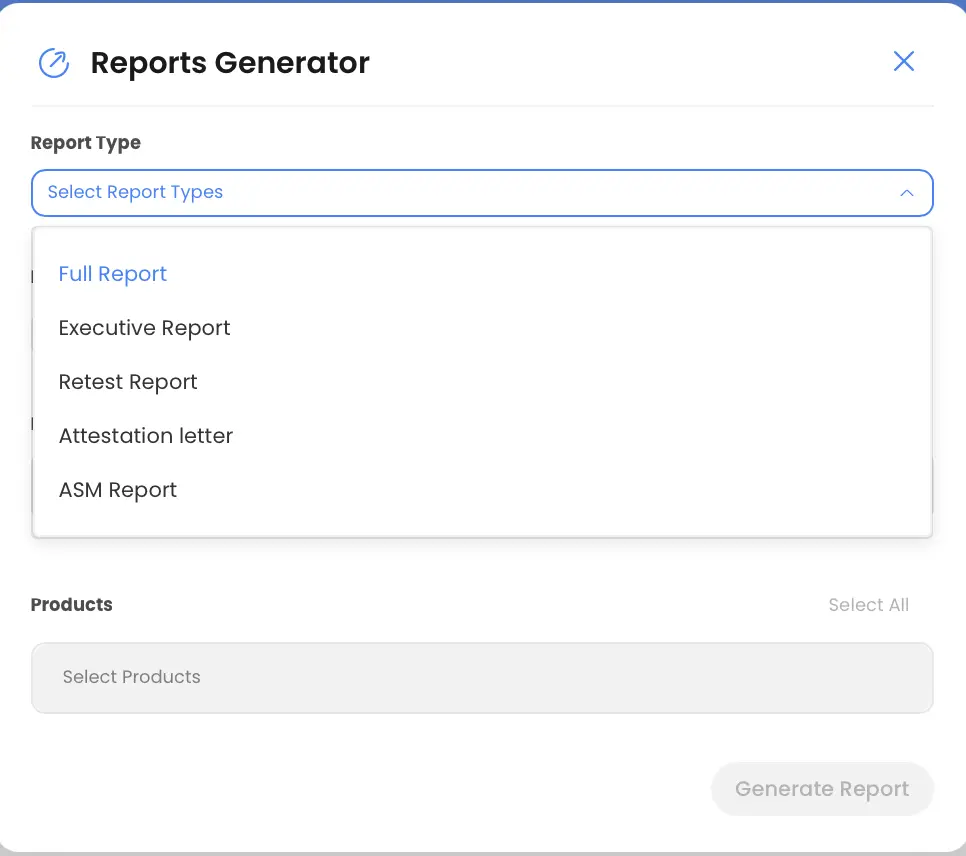
DevSecOps Integration & Collaboration
For security to truly scale, it needs to align with the way development teams work. That means embedding testing and remediation into the existing tools, workflows, and cadence of your DevOps pipeline, not forcing teams to operate in silos or wait on external reports.
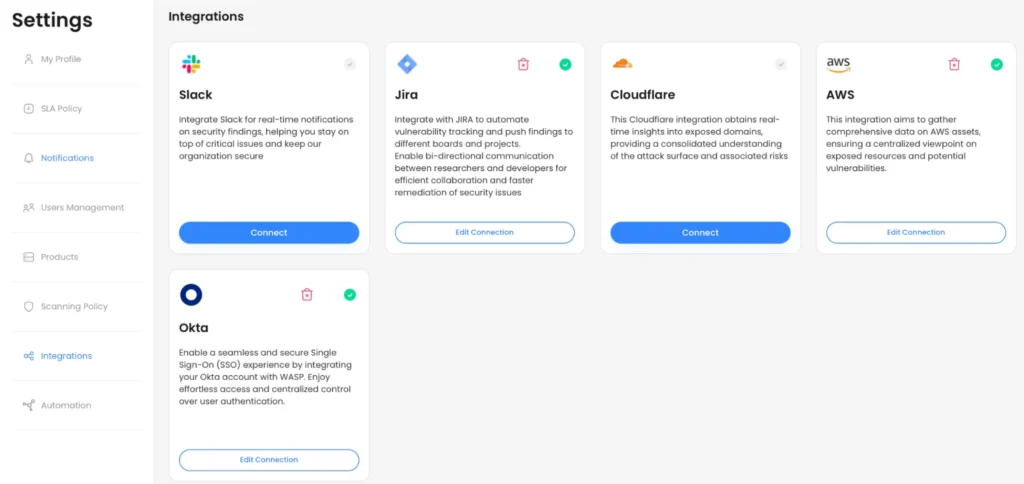
Key integrations include feeding findings into issue trackers (Jira, GitHub, etc.) and chat tools, and having dashboards that present live security metrics.
These features keep developers and security teams aligned. The platform should allow pentests on demand (or scheduled) at any stage of development, preventing security issues from accumulating. Early testing means fixes before release, avoiding expensive late rework.
- Workflow Integration: It must connect with your toolchain (ticketing systems, version control, CI tools) so that vulnerabilities flow directly into your backlog. WASP, for example, integrates with Dev workflows and lets you retest fixes instantly via the platform.
- Team Dashboards: Both executives and engineers should have access to live dashboards. These should show trend graphs, outstanding issues by severity, and progress over time. Integration with existing cloud and tech stacks is a plus.
How WASP excels: WASP is designed as a DevOps-friendly PTaaS. It instantly delivers findings into your workflow, so developers receive alerts where they work (e.g., ticket system) and can request immediate retests.
With this developer-friendly approach, WASP can cut MTTR by up to 75%. WASP supports popular tools out of the box, with the possibility to create custom integrations from scratch or use ones created by the community.
Try WASP, OP Innovate’s PTaaS Platform
If you’re a CISO or security leader evaluating PTaaS solutions, remember these criteria: continuous coverage, expert testing, actionable output, DevOps alignment, and scalability.
OP Innovate’s WASP platform embodies all of these best practices, combining certified manual tests, 24/7 attack surface management, and seamless workflow integration.
To see how WASP can strengthen your security program, create your FREE account or contact us for a guided demo of the platform.










