It would be great if we could always learn from positive experiences. Unfortunately, in life and in cybersecurity, it’s often mistakes or challenging situations that give us the best lessons that drive change and improvement
Recently, the OP Innovate team was approached by a CEO in a panic after they noticed some suspicious login sessions in their web application. Let’s take a closer look at the incident and the lessons we can learn to prevent similar scenarios in the future.
Incident overview
Speaking with the OP Innovate team, the CEO explained that their web application had experienced five logins using valid usernames and passwords on the first try. One of their developers noticed that the connections originated from an Asian country, even though their clients are based in Germany.
The CEO expressed concerns that their client database and passwords may have been exposed, To add even more stress to the situation, the affected organization was in the middle of an M&A term sheet.
Response and investigation
In these scenarios, speed is of the utmost importance. The sooner you detect, respond to, and mitigate the threat, the less damage it can cause and the faster you can restore normal operations.
Recognizing the gravity of the situation, the OP Innovate Incident Response (IR) team immediately sprung into action. The investigation team consisted of:
- An IR team leader who managed the crisis and coordinated efforts.
- A forensic researcher who investigated endpoints, logs, security tools, etc.
- Penetration testers who analyzed the client’s login page and searched for possible leaked credentials on the Dark Web.
Our team also utilized our WASP platform to uncover all external-facing assets of the organization. WASP leverages automated discovery mechanisms like web crawling, DNS enumeration, and IP scanning to map an organization’s entire digital footprint
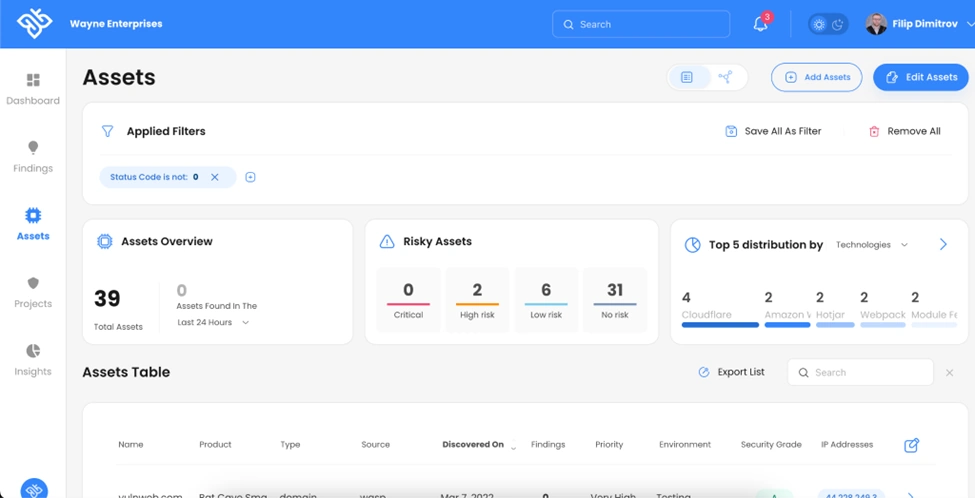
The “Assets” view within OP Innovate WASP
Want to see WASP in action for yourself? Create your free account now.
Discovery and findings
After a few days of extensive investigation, our security experts found all five users with valid logins in an infostealer database on the Dark Web. It’s likely that a malicious Advanced Persistent Threat (APT) actor used advanced phishing techniques to trick employees of the victim organization into installing an infostealer.
The infostealer then successfully exfiltrated login credentials, which were subsequently used to gain unauthorized access to the organization’s systems.
Understanding infostealers
Infostealers are a type of malicious software (malware) designed to covertly capture and exfiltrate sensitive information from an infected system. These programs can collect a wide range of data, including login credentials, as in the case of our client, but also financial information (crypto wallets), personal identification details, and other forms of sensitive data.
The exfiltrated data is then usually used for fraudulent activities, including identity theft and financial fraud, or sold on the Dark Web.
As you can imagine, you don’t want this kind of information being leaked on the internet for everyone to see. Nor do you want credentials to your organization’s internal systems being compromised in this way. Unfortunately, the incident our client suffered is far from isolated.
Thousands of company accounts for services like Google, Microsoft, and others are readily available on the dark web, sometimes selling for as little as $10. It only takes one bad actor obtaining these credentials to inflict serious damage on an organization. The consequences can range from data breaches and financial losses to severe reputational damage.
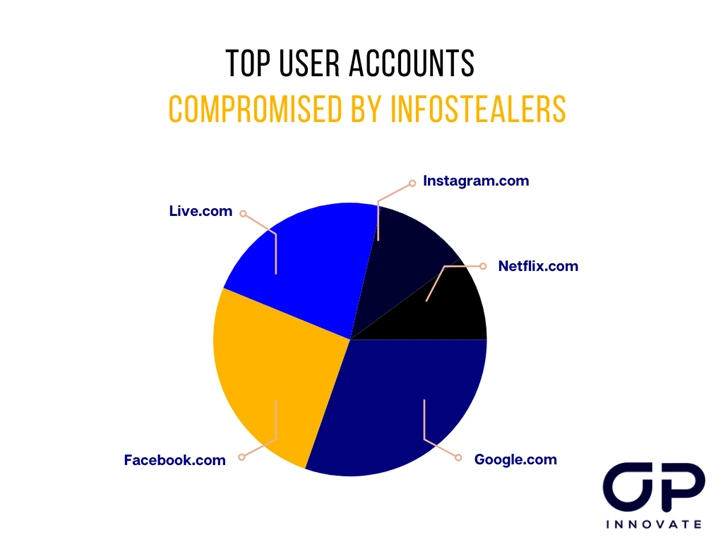
Source: Hudson Rock
How to protect against infostealers
Considering the significant threat posed by infostealers, organizations must implement proactive measures to safeguard their sensitive information and maintain robust security. Here are some essential steps for companies to protect against infostealers:
Train employees on cybersecurity awareness and phishing prevention: The majority of cyber incidents are the result of human error. By educating employees about common phishing tactics, and the importance of cautious behavior online, organizations can significantly improve their security resilience.
Implement strict authentication policies: Require users to use strong, unique passwords and enable multi-factor authentication (MFA). This way, even if cybercriminals manage to obtain login credentials, the additional layer of security provided by MFA will make it significantly harder for them to gain unauthorized access.
Keep software and security tools up to date: Regularly update all software and security tools to ensure that the latest security patches are applied, protecting against known vulnerabilities.
Understand your attack surface: You can’t protect what you don’t know exists. Regularly audit and inventory all external-facing assets, including websites, applications, and databases, to ensure comprehensive visibility and security coverage. Utilizing tools like OP Innovate’s WASP can help identify and manage these assets effectively, reducing potential vulnerabilities.
Secure your organization with OP Innovate WASP
Defending against modern security threats like info stealers and other malware requires an innovative approach. That’s exactly why OP Innovate created WASP – the most comprehensive web application security platform on the market.
WASP continuously monitors your external attack surface, providing observability to the application’s security posture. It proactively identifies the risks resulting from the exposure of new technologies and the known and unknown expansion of your digital attack surface.
One of WASP’s key features is Attack Surface Management (ASM), which combines the efficiency of automation with the expertise of our top offensive security experts, ensuring your organization stays one step ahead of cyber threats.
Sign up for your free account now and enjoy unparalleled visibility and protection for your organization’s assets.









