In cybersecurity, a false positive occurs when a security tool raises an alert that either points to a threat that does not exist or assigns the wrong level of urgency to a legitimate event. This misfire often stems from missing context, such as not knowing an asset’s business importance, or from misinterpreting routine behaviour as malicious activity.
Despite significant advances in automation and detection tools, the signal-to-noise ratio remains dangerously off balance. Analysts are still spending hours chasing alerts that lead nowhere. Over time, this constant flood of non-issues leads to alert fatigue, slower response times, and worst of all, real threats slipping through the cracks.
Why False Positives Are Still So Prevalent
Here are just some of the reasons false positives have remained a prevalent issue for security teams in 2025:
Over-Reliance on Automation Without Human Validation
Security stacks today are packed with tools that generate alerts based on signatures, heuristics, or behavioral anomalies. But without expert validation, many of these alerts are theoretical risks at best and completely benign at worst. When every anomaly triggers a red flag, security teams are left to play whack-a-mole with alerts that never had real-world impact.
Poor Correlation Between Alerts and Actual Risk
Most tools lack the ability to weigh technical vulnerabilities against the real-life business impact. A critical vulnerability in a test server may not matter, while a medium-severity issue on a public-facing production system could be catastrophic. Without this correlation, teams are forced to triage based on severity scores that don’t reflect true risk.
Lack of Context
An alert that doesn’t take into account asset value, business function, or exposure level isn’t actionable. Security teams need context to prioritize: is this system internet-facing? Is it part of a critical application? Is it even in use? Most tools don’t provide these answers natively, forcing teams to do the extra legwork.
Alert Fatigue Is Real (and Dangerous)
When everything is labeled “critical,” eventually nothing feels urgent. Over time, security teams become numb to the noise. This alert fatigue often leads to real threats being ignored or buried under a mountain of non-issues. A recent 2024 Devo SOC Performance Report found that up to 53% of security alerts are false positives, and 70% of SOCs struggle to manage the alert volume.

The Impact on Security Teams
- Mental and operational fatigue
- Slower incident response
- Critical issues buried in noise
- Security teams spending more time triaging than remediating
- Difficulty justifying security ROI to leadership
By the Numbers: False Positives’ Impact on Security Teams
Recent studies confirm that false positives continue to cause significant disruption in cybersecurity operations. Despite technological advances, most organizations are still struggling to effectively reduce noise in their alert pipelines.
In some environments, false positive rates can exceed 99%. For example, in a monitored oil refinery setting, intrusion detection systems (IDS) generated nearly 27,000 alerts, but only 76 of them were legitimate. That’s a false positive rate of over 99.7%.
False positives typically result from:
- Overly sensitive detection algorithms
- Misconfigured security tools
- Anomaly-based systems misclassifying unusual but harmless behavior
- Lack of contextual enrichment
- Outdated threat intelligence feeds
These false alerts have real business consequences. Many organizations report automatic defensive actions triggering unnecessarily, such as isolating devices or disrupting services, simply because a non-threat was misclassified as malicious.
In a 2023 industry survey (by Morning Consult and IBM), SOC professionals reported spending approximately one-third of their workday investigating alerts that are not genuine threats, and about 63% of daily alerts were considered false positives or low‑priority, corresponding to a workload of over 10 alerts per day with over half being non-actionable
Despite growing adoption of AI and integrated detection and response architectures like SOAPA, many organizations still face interoperability challenges and underutilized tooling. Over 36% of security professionals recently surveyed said they are overloaded by false positives, and a large portion voiced concerns about the continued unreliability of their detection systems.
How OP Innovate Reduces False Positives to Expose Real Threats
At OP Innovate, we’ve seen firsthand how damaging false positives can be, not just to operations, but to morale and long-term security outcomes.
That’s why our approach to penetration testing and vulnerability management is designed from the ground up to eliminate noise and surface only what matters.
Human-Validated Testing
Our Penetration Testing as a Service (PTaaS) model, powered by WASP, doesn’t rely on automation alone. Every finding is manually validated by experienced security professionals. That means no chasing phantom threats or wasting cycles on vulnerabilities that don’t pose real-world risk.
Context-Rich Reporting
Through our WASP platform, every alert comes with detailed context: asset value, business impact, exposure level, and exploitability. We don’t just tell you what was found. By understanding not only the technical details but also the potential consequences for your business.
From regulatory exposure to operational disruption, your team can make faster, smarter decisions and prioritize the issues that truly matter to your organization’s security and continuity.
Built-In Triage and Retesting
WASP includes tools for triaging, retesting, and resolving vulnerabilities directly within the platform. No spreadsheets, no ticket ping-pong, just actionable insight with everything in one place.
Security-Engineering Collaboration
We designed WASP to bridge the gap between security and development. Teams can communicate directly in-platform to clarify findings, request retests, and confirm fixes, cutting time-to-remediate by up to 75% while reducing friction.

What Happens When You Cut False Positives?
Tuning out the noise does more than ease analyst workload. With fewer distractions, true positives rise to the top, allowing critical vulnerabilities to get the attention they deserve. In WASP, every finding is categorized based on severity (from informational to Critical).
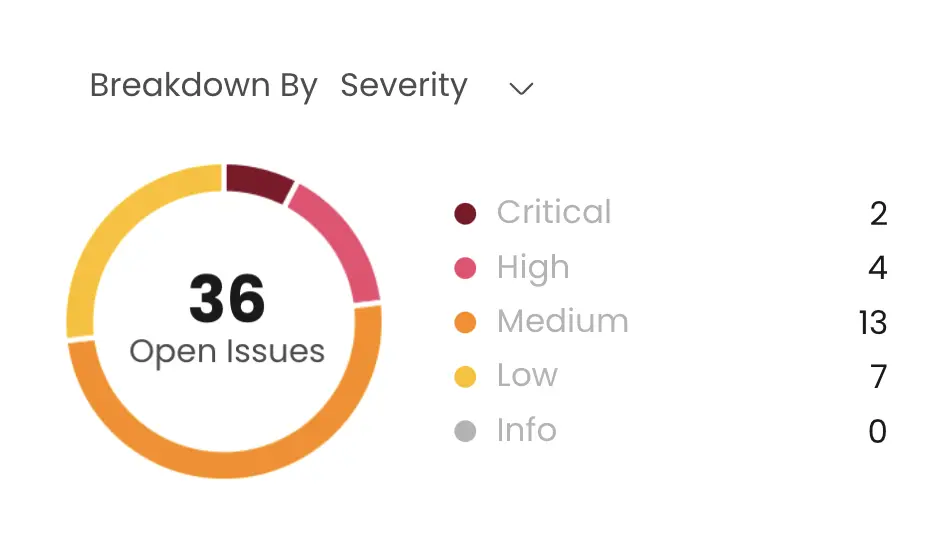
But the benefits of reducing false positives aren’t just operational. When security teams are no longer stuck in a reactive loop, they regain time for strategic work like threat hunting, purple teaming, and strengthening incident response playbooks. This shift from alert triage to proactive defense fosters a more motivated, empowered team.
The result is a security program that’s leaner, faster, and far more aligned with business risk. Instead of being buried in low-value alerts, teams can focus on meaningful action and improving resilience.
Cut Through the Noise With WASP
Is your team drowning in alerts and struggling to separate signal from noise? If yes, it might be time for a new, smarter approach.
At OP Innovate, we built WASP to help security teams focus on what matters. By combining manual expertise with intelligent automation, WASP triages alerts, filters out false positives, and prioritizes real threats so your analysts can respond faster and more confidently.
Stop wasting time on noise. Start acting on what’s real. Book a demo to see how WASP can transform your threat detection and response, or create your FREE account now.










